An Avast team calling themselves the Security Warriors, comprised of intra-departmental specialists, are running experiments in the streets of San Francisco. They spent a few days setting up the first of them and have already gathered some interesting statistics. In Filip‘s words, here is what they have done so far and what they want to achieve.

Filip Chytrý , president of mobile Gagan Singh, Bára Štěpánová, Jaroslav Slaby, and Vladislav Iliushin. Not pictured: Ondrej David
One of our first experiment’s objectives is to analyze people's behavior by seeing how they have their devices preset in terms of outside communication. We didn't have to go far to find out – it's pretty disturbing. Currently, we have a variety of devices prepared for different traffic experiments but now we are using them for one really easy target - to analyze how many people connect to a fake hotspot. We created fake Wi-Fi networks called Xfinity, Google Starbucks, and Starbucks. From what we've noticed, Starbucks is one of the most widespread networks here, so it's pretty easy to get people's devices to connect to ours.
Wi-Fi networks screen
What is the problem we're trying to point out?
Once your device connects to a known SSID name at your favorite cafe, the next time you visit, it will automatically try to connect to a network with the same name. This common occurrence becomes a problem because it can be misused by a hacker. Armed with some basic information, a hacker can figure out what you are doing and even which device you have. It is just a matter of time to come up with the right technique to hack into your device. After a day of walking around with my tablet, we gathered some telling statistics.  From data we gathered in seven hours, we found that 264 people connected to our fake Wi-Fi networks and generated 512,000 data packets*.
From data we gathered in seven hours, we found that 264 people connected to our fake Wi-Fi networks and generated 512,000 data packets*.
- 52% connected from an Apple device
- 42% connected from an Android device
- 10% connected from a tablet or notebook
Percentage of traffic distribution generated from those devices
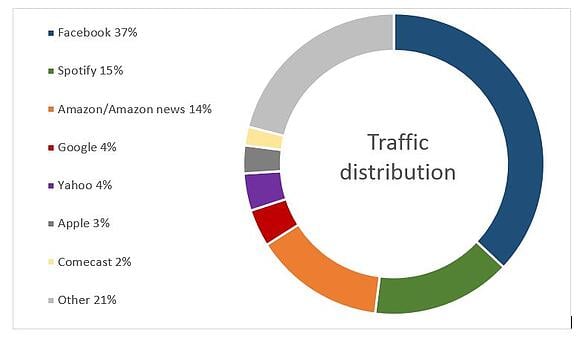
- 70% of them have the Facebook app installed
- 30% of them have the Twitter app installed
- 30% of them accessed a Google-related service
- 20% browsed a webpage
What is on our tablet?
The device used for this experiment is a pretty simple off-the-shelf Nexus 7 with a rooted LTE modem. We set up fake hotspots and used tools to catch TCP dumps. Later on, we analyzed who was doing what. Nothing hard at all. Our hotspots are movable, so I have one tablet with me at all times with a fake Wi-Fi network called Google Starbucks. If you see that hotspot somewhere in town, you might want to watch your device more carefully. ;-) Did I mention we did this using only a tablet? We do have a couple of other things up and running, but that‘s something for another blog.

Traffic flowing over the Golden Gate Bridge
If you want to be involved and aware of how these things work, you can catch up with us in San Francisco. Up until now, we have let the traffic flow as it should and gathered data, but next, we‘ll play a bit with redirection. :-) *A packet is the unit of data that is routed between an origin and a destination on the Internet or any other packet-switched network.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.