Does the title of this blog post have a mysterious meaning? Not exactly.
In this first part about the gray-zone of Android malware detections, I will introduce the Android:SecApk, a detection regarding the protection that the App Shield (Bangcle) offers to Android applications (.apk). This detection has a big sample set that is still growing. Some SecApk wrapped samples that existed or still exist in the Google Play Store and third party stores, can be seen in the table below.
|
MD5
|
Name \ Info
|
|
F1EF5B8C671B2146C2A2454ECF775E47
|
G锁屏冰雪奇缘之来自星星的你V1.0.apk
\ PUP – An application to promote a specific movie. Potentially unwanted because of the extended permissions that was requested.
Current Status: Removed from Google Play
|
|
10bd28d4f56aff83cb6d31b6db8fdbd2
|
Cut_the_bird.apk
\PUP – A game that have potentially unwanted permissions that they can drive to loss of private personal info.
|
|
05ffb6f34e40bb1cf8f9628e5647d5e3
|
aini1314langmanzhutisuoping_V2.5_mumayi_700e0.apk
\PUP – A screensaver application that has permissions unrelated with the purpose of the app.
|
|
d6b40bbb79b54c09352a2e0824c0adba
|
3D职业乒乓球.apk
\Pup – This application is a tennis game. Potentially unwanted because of the extended permissions that was requested.
|
|
eefd2101e6a0b016e5a1e9859e9c443e
|
eefd2101e6a0b016e5a1e9859e9c443e.apk
\Malware – This app steal personal data and SMS messages from the user.
|
The App Shield is an online service that, after a submission of an .apk, encrypts it and adds some layers of protection. The procedure of the encryption and protection of the apk will be discussed with more detail during the course of the second part of this blog post.
Starting with the submission process, a clean app named AvstTest.apk uploaded to the service. The exported .apk was renamed as AvstTest[SecApk].apk. In addition, apktool and dex2jar used accordingly to decode the .apk resources and convert the ‘.dex’ files to ‘.jar’.

The internal file structure of the converted apk change can be seen in the picture above. Two new folders appear; ‘lib’ and ‘assets’. The ‘lib’ folder contains two files that are required for sharing library files for the ARM platform.
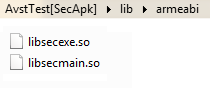
Next, the assets folder contains an encrypted jar file named ‘bangle_classes.jar’. This file is an encrypted version of the original ‘classes.dex’ file. Also the ‘meta-data’ folder contains files that are required for RSA encryption.

The Android manifest file is changed as well, but only for the purpose of linking the new dex file main application subclass. This class (com.secapk.wrapper.ApplicationWrapper) will be instantiated by default whenever the process is started.
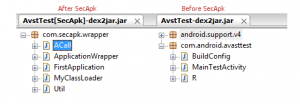
The internal structure of the ‘classes.dex’ file is also changed. In the new dex file, we can see the new class ‘ApplicationWrapper‘ that is being used to load the unencrypted version of the original ‘classes.dex‘ file in the memory. The original dex file structure can be seen in the right part of the image below.
The real concern of this blog-post is that every file that uses this protection must be detected as a PUP (potentially unwanted program). Many malware authors use this protection to make their malicious samples undetectable. In parallel, legitimate applications use the protection to stay away from disassembling, decompiling, injection of malicious code, and other illegal uses.
This is the gray-zone.
The company that created this protection states that every file is checked by various virus definitions. The problem is that zero-day malware exists and some of them are really hard to detect. In the case that malware protected by SecApk was inserted into an official market place, they will be difficult to be detected. The safest choice is to detect the SecApk wrapper and inform the user, that the application that is going to execute is potentially unwanted.
The second part will explain with more detail the process that this wrapper uses to load the original unwrapped code in the memory of the system.
AVAST protects Android users
Avast! Free Mobile Security detects and warns the user about those applications (malicious or not) that are wrapped with the SecApk wrapper and may be potentially harmful. Still there is no other way to efficiently protect our customers and a good tip is to rethink using those kind of protectors for your applications.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.