Pretty women. Which one will infect you?

Malware which opens pictures of attractive women to entice its victims has been around for some time. Last month there were more than usual, so I decided to research malware that pretends to be a regular picture, and the results are pretty interesting.
We looked for executable samples with two distinct characteristics: 1. .jpg in their name, and 2. no older than the last three months. About 6,000 unique files which matched this criteria were found. From these samples, we noticed that pretending to be an image is not a family specific criteria but we identified that Win32:Zbot is represented more than other malware e.g. MSIL:Bladabindi-EV, Win32:Banker-JXB,BV:Bicololo-CY, etc.
The important message is that most of these samples are distributed by scams which are sent by email or posted on social media sites. An example of an email scam is pictures below. If you are interested in what the social media scam looks like and how to protect yourself, you should read one of our previous blog posts.
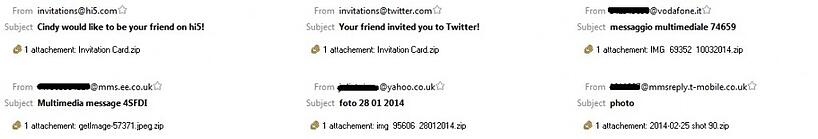
Picture openers
As I wrote in the introduction, the main motivation is malware that actually opens a picture. This is a smaller group - about 10% of the whole search. In the sample group, we discovered that the malware doesn't open only pictures of women - surprisingly, pictures of men were used too, but images of women are leading over men at a ratio of 14:3. We spotted non-sexual images, but they are not very common.

The interesting thing is the source of image. Using an appropriate search engine, we were able to identify some of them. Their origin were social media profiles (Facebook, Instagram) and personal blogs. That actually confirms that publicly accessible images can be very easily abused.
Technical details
Most of the samples are obfuscated MSILs with file size between 200-1024kB. When the user executes that file, a picture is shown in their default picture viewer and malware is dropped and executed in the background. One interesting example works in teh following way:
It unpacks a downloader from the resource image using XOR with a hardcoded 11byte key and then executes the unpacked MSIL assembly.

Read more about malware dropped from a bitmap picture here.
The configuration static fields found in the unpacked assembly suggest usage of a generic dropper. We discovered that it is a part of KazyCrypter. This one is all in one dropper and downloaded. At first, data are unpacked from gzip resource, which in this case is an image of a woman that is dropped and 'executed' which leads in opening the default picture viewer. Then the payload(s) is downloaded and executed from link(s) specified in DownLocations array and saved to location(s) in DownNames array.

Some SHA256
ADA8229CE99B8386E89EB94ECAB678AE79C8638B3EAF3532B847CFF2B201C232
280F505FC44740913CAA423195F0309B412EDB58977D3E9A457539D148947875
283347FA340C8535A7830C9FF14F01E75B3E190144AB7C1E90667C49F9FEF425
C6CA2E3A33AD488B6B386F304E325BDBD549D5ACF7583732E85516DCD5790D38
Conclusion
Malware distribution through scams is fairly common. Don’t be fooled, use your brain! Protect your privacy and don’t publish your pictures unless you really have a good reason to. Who knows if your images or those of your family members will be abused in malware which can infect you and others.
Acknowledgement
The author would like to thank to Peter Kalnai and Jaromir Horejsi for their help and consultations related to the topic.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.