A new threat for the Linux platform was first mentioned on August 7th by RSA researchers, where it was dubbed Hand of Thief. The two main capabilities of this Trojan are form-grabbing of Linux-specific browsers and entering a victim's computer by a back-door. Moreover, it is empowered with features like anti-virtualization and anti-monitoring. With the level of overall sophistication Hand of Thief displays, it can be compared to infamous non-Windows threats such as the FlashBack Trojan for MacOsX platform discovered last year or Trojan Obad for Android from recent times.
A detailed analysis uncovers the following structure of the initial file with all parts after the dropper being encrypted (hexadecimal number displays starting offset of a block):
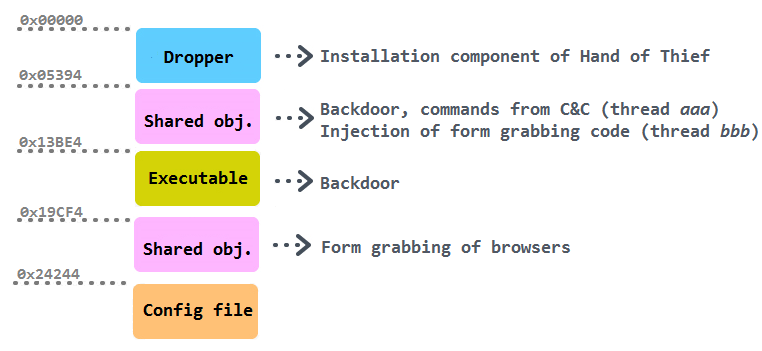
Running the program on a native Linux system with parameter "-v" displays the version info "0.1.0.7".
Dropper and Self-Protection
The dropper is obfuscated with the UPX packer so the executable is not available for a static analysis. We make it so by applying the original UPX program with parameter -d on a sole dropper part of the initial binary. The readability of almost all character strings is hardened by a XOR encryption with a varying 8-bit key. This is a very common property shared both among Windows and non-Windows Trojans.
Immediately after start, the Trojan checks if it does not run in a virtualized environment. Realization of this aim depends on virtualization software: To search for a substring "VBOX" and "VMware" in the listed SCSI devices (to suppress this check it is enough to unset read privileges on the file /proc/scsi/scsi ); to look for a substring "UML","PowerVM Lx86", "QEMU" or "IBM/S390" in /proc/cpuinfo file; to check an access to /proc/vz or /proc/bc which exist if OpenVZ kernel is running:
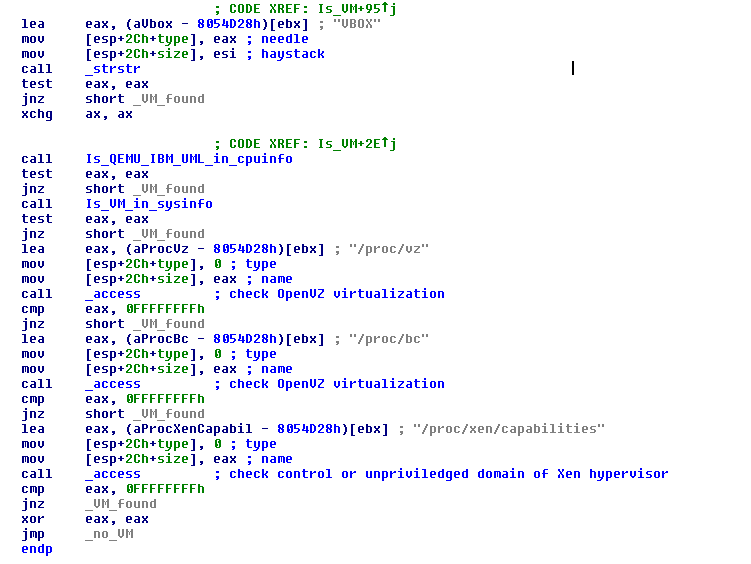
The presence of any of these signs leads to an early end of execution. The Trojan also exits if the root directory is chrooted by comparing particular lines in /proc/1/mountinfo and /proc/\<getpid()>/mountinfo. Chrooting is basically a security feature where a running process does not have access to the root directory but to another branch of a file system tree that acts as one.
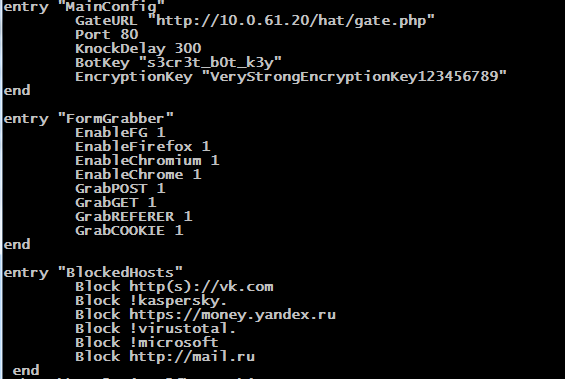
Then it decrypts the config file appended at the end of the binary (starting on the offset 0x24244 with the length of 0x1E0) and it initializes its global variables with entries from the config file (values are resolved using regcomp, regexec and regfree command). We analyzed a sample with the following one (a private IP serving for C&C whispers that this bot is in debug process and not in the wild):
To achieve persistence after reboot, the Trojan is suspected to create a configuration file called system-firewall.desktop within the path ~/.config/autostart containing the following setting (%s is appropriately changed):
[Desktop Entry]
Encoding=UTF-8
Type=Application
Exec=%s
Terminal=false
Name=System Firewall
StartupNotify=false |
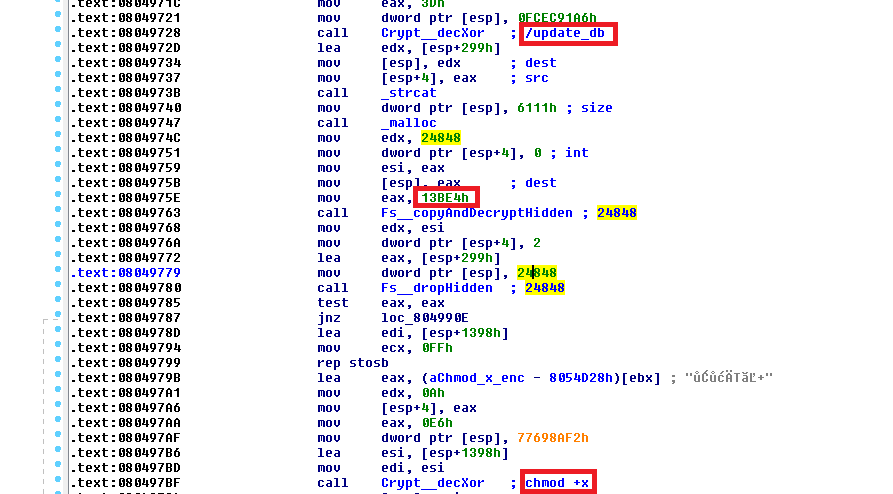
The step that follows is the installation of modules containing the main functionality into the /tmp/ directory and changing access permissions with a command chroot with parameter -x. The procedure consists of mapping the binary into the memory and copying a relevant part to a buffer that is decrypted by AES with a 256bit key. For the executable of a length 24848 it is performed like this (the marked values denote the target file name, the starting offset in the binary and the access permission):
The shared object is injected in every process whose name does not contain substring gnome-session, dbus or pulseaudio. The injection is performed with a method similar to the one described on Blackhat 2001 by Shaun Clowes. The reimplementation is available on github.
Core Functionality
The shared object starts two threads. The first one is called aaa, and it listens to a command from C&C to execute an action: bc command triggers BackConnect daemon called p0stfix serves as a reverse shell with a victim connecting to a particular socket; bind command starts BindPort daemon called unix-daemon acting as a bind shell with an attacker receiving the content of an output of a shell (after the correct authentication); socks executes a proxy via custom implementation of SOCKS5 protocol. All these features are realized through embedded perl scripts. Another commands with names d_exec and update, and they would try an execution of newly downloaded files from a C&C server.
The second thread is denoted bbb. It performs the injection of the shared object starting on the offset 0x19CF4 into running browsers mapping space by the same method mentioned above. This serves as an initialization of the form-grabbing feature. Supported browsers are Chromium, Chrome and Firefox. The intervention of data submits of the Firefox browser is realized as the redirection of program flow of original libnspr40.so!PR_Write function to a custom implementation hPR_Write_ptr of Trojan:
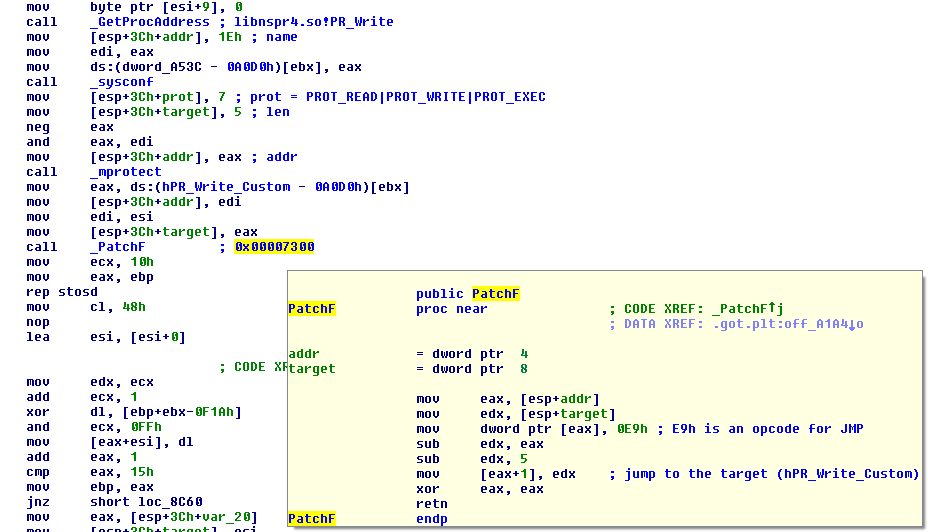
Intercepted data, statistics of bots execution, and command from C&C are all interpreted via a custom communication protocol based on AES encryption with 256bits keys combined with Base64 encoding:

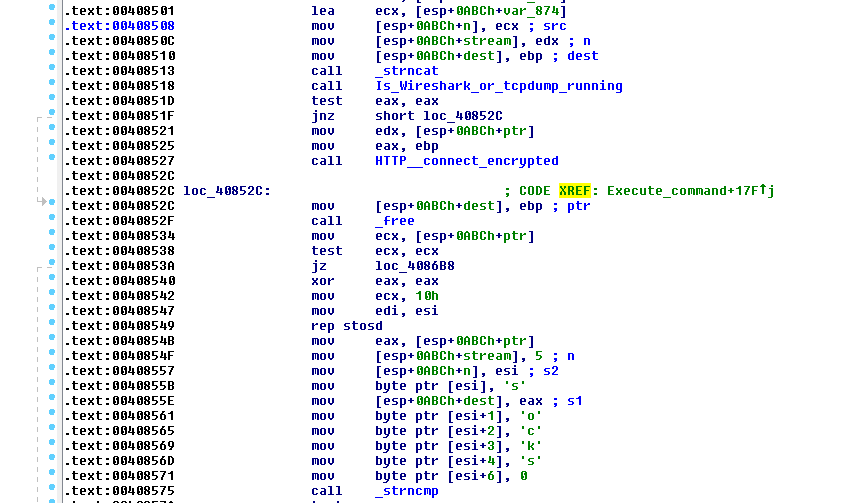
Moreover, we observed an anti-monitoring check (no communication if wireshark or tcpdump is running):
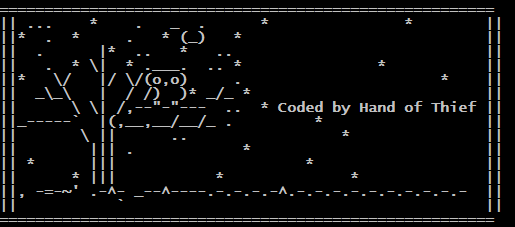
Finally, the exported function drow_image displays an about info in a form of nice ASCII art that confirms the creativity of the author (an owl sitting on a tree can be recognized):
Conclusion
The Linux operating system is designed to have high level of security. However, this year a few attempts to attack Web servers by backdoors redirecting traffic or malicious apache modules have been discovered. The aim of this Trojan is to compromise user desktop systems. With features designed to abuse sensitive browser information, it could advance Linux users a step forward in this specific environment. The same threatening environment in which Windows users have existed for years. The statement that the Linux platform is absolutely secure now seems even more illusive.
Sources
SHA256 hashes of some selected samples:
Acknowledgements
Thanks goes to my colleague, Pavel Šrámek, for discussions about the Linux platform.
Add your comments here, or read what others have to say on the AVAST Facebook page.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun, and contest information, please follow us on Facebook, Twitter, Google+ and Instagram.