It has been two or three months since I last blogged about Android malware. But that definitely doesn't mean there aren't any new threats. There are plenty! Here are two quick comparisons from the last two years: Growth of the malware problem of the platform in January 2012 compared with January 2013 is far from the 'normal' growth of other platforms. According to our statistics, it's something around +850 percent! Add another year for an even more insane comparison - the growth from January 2011 to January 2013 gives us +3150 percent! The Android platform is definitely one of the most targeted malware platforms these days. But no worries, users of Avast! Free Mobile Security are safe.
Because this is the technical part of the blog, I should tell you a bit more about some malware. I picked one type of the infected apps which came to our Virus Lab lately. A really popular form of malware delivery is the use of a proper and well-known clean application. Malware creators add some small code, which may not be harmful at all, for example, a small downloader. But these few lines of coding can create a mess in the end. That's the problem with an application below.

This app is a Chinese game where you drive a car and collect points to get the highest score possible. The game is actually pretty fun, if you are unaware of the small downloader inside running in the background. Without your notice, the application downloads another installer called @GameToolz. And that's when it gets interesting! But I'm a little ahead of myself...
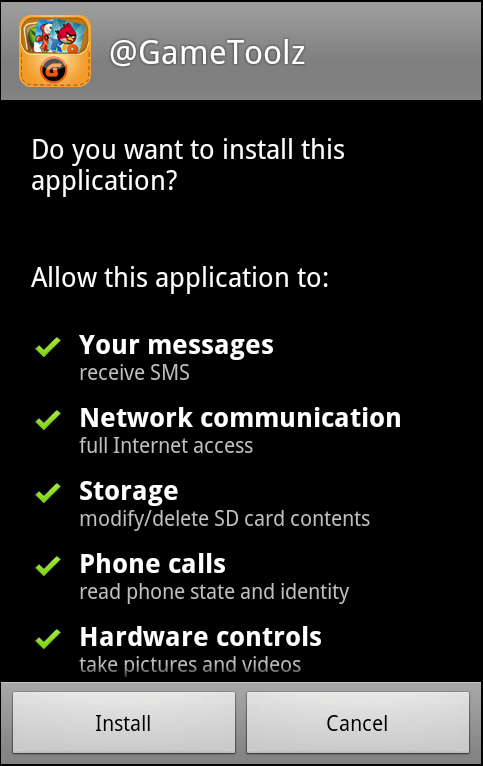
As you may have noticed from the screenshot above, this application has some weird permissions. For example, SMS access or hardware control is definitely suspicious. But even if you don't agree with the installations, it's too late - the application/infection is already installed. This application is downloaded under the name DWQB or GAMESNS from the following URLs which are encrypted in the first infected application.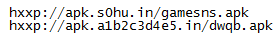
In the end this downloaded application will collect data about your phone, such as the SIM serial number, IMEI, phone number, device model, OS version and so on. They are packed and sent quietly to the malware creator. It doesn't sound so harmful, does it? But the part with the potential threat will follow. The application is run in the background of your Android device so it's ready to take remote commands from the malware creators. You never know when this worst part will be used against you. They can install what they want remotely, without your knowledge . So in just a few minutes your phone could be sending paid SMS without you knowing it, or they can steal your passwords and basically do whatever they want.
Avast! Mobile Security detects all of the mentioned stuff connected to this application. The first samples with the small downloader are detected as Android:GinMaster-ABM; the downloaded applications as Android:GinMaster-ABN and URLs are blocked by Avast as well. There are hundreds of samples like this one which have this small downloader inside but all of them lead to the two links mentioned above. And where we found those infected applications? Well just try to go through some of a download servers or Android blogs. I'm quite sure, one of fours applications there will have some similar malware code inside. So if you want to be sure you don't have something similar in your phone, I recommend you to scan your device with Avast! Free Mobile Security.
SHA:
3696C5C264FC26EB46F63C37F484B96C8D54C0D94E125C40B8601483420F54C1
3E376423BA4B1CFB14E6BE2E73979D5DC8FF68943A668FA4CB70449F0B485BC8
4094B724D43BCAA8ABDEE34C5E26CD3DC3E30BAB1EEE050E4F8BFFA4D2AADA0F
Downloaded apps SHA:
9CD1711AB3A0DAC3F7AB5957D19BDD0CB5C665BF05BC4836D16FF9E38EBFC419
F99891707F0A3D7EA003132598CAE4D277922BED2DB520A2DE008565E2C09D50