New vulnerabilities in the Oracle's Java Runtime Environment (JRE) have been recently discovered in the wild (first vulnerability originally reported by Fireeye, the second described by Esteban Guillardoy). The vulnerabilities targets newest version of JRE (1.7) and even with the latest update (JRE 1.7 update 6) your machine is in danger and easily exploitable. According to the Oracle’s patching cycle the patch is out of sight. So scary and Java again! But it is even worse!
The most successful exploit kit has quickly adopted these bugs which was predicted by the Brian Krebs earlier. So, all the current Blackhole campaigns use these exploits in order to infect victims. In addition, the exploitation is confirmed to work using Internet Explorer, Firefox, Opera, Google Chrome and also Safari on multiple platforms including Windows, Linux and MacOS.
Do you really think this can't be worse? Oracle knew about these (and also other) vulnerabilities since April according to the Adam Gowdiak, the founder and CEO of Polish security firm Security Explorations.
The blackhole exploit kit was the first, but not the last! We have also identified other exploit kit adopting this exploitation in the wild and others would follow soon, for sure. The Nuclear Pack exploit kit added support for successful exploitation of the latest JRE vulnerability. Interestingly both mentioned packs use the same principle and serve two latest Java vulnerabilities (CVE-2012-1723 and CVE-2012-4681) together inside one single jar file. This allows attacker to attack all environments (up to JRE 1.6 and JRE 1.7) with just one applet tag included inside the landing page of the proposed exploit kit.
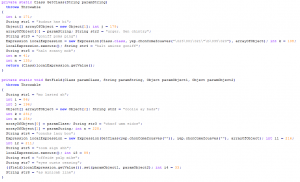
The newly discovered adoption uses slightly bigger obfuscation in comparison to the Blackhole or also in comparison to the original exploit found in the wild. The random numeric and string constants used in the code just try to confuse detection engines and make the exploit undetected. Also all important string constants are encoded in this variant. The overall detection might be seen on virustotal.
We will see more sophisticated hiding techniques in the following weeks as the main achievement for the Black Hats would be totally undetected sample by the all AV’s around. We will thwart theirs plans by releasing generic detections and using behavioral and dynamical detection mechanisms – we will simply do the best to protect our users. However, I would suggest removing the JRE if possible or at least turning it off in all your browsers. Please follow Brian Krebs notes on how to unplug the Java from your browser.
We will hopefully see appropriate steps taken by the Oracle resulting in the patch in the next few days - the patch should be already done according to the time Oracle has known about this problem.
Just as an addition, similar story has been released few moments before publishing this article: Sakura exploit kit is just about to adopt the new vulnerability.