The Android:FakeInst family of malware seems to be never ending story. Its creators have been trying to trick users into sending premium rate SMS messages for several months now. Just a few days ago, we discovered 25 more apps placed on alternative markets that are all based on very similar concepts as was the one in the story we wrote about before Christmas.
This time malicious Android applications are hosted on several domains:

All these sites were registered a week ago so it looks like they were supposed to serve as a malware hosting for the bad guys from the very beginning. Also if someone tries to access these sites from the browser, the visitor only receives a 404 error message which does not look like a legitimate site. Analyzing the trail the malware creators left for us, we’ve discovered a few sites they have used in order to attract users and all of them target Russian speaking people and look like an alternative markets. In reality, these sites exist for a short period of time and offers only fake downloaders.
So what does the visitor see? A user is tricked into installing an application called Downloader with suspicious permissions which shows a screen with two buttons entitled OK and Rules. Clicking on the Rules is an entry to a one way road where the authors inform the victim that the download can cost some money. At this point, it claims that it is now possible to either agree or quit by clicking on the relevant buttons. But this is lie because clicking on quit does nothing at all. So you have to give up and click on Agree or OK on the first screen and then the scam begins!
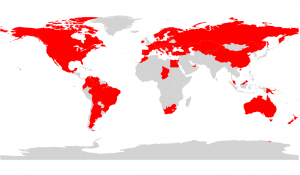
And this scam costs you money! As If somebody clicks on the OK or Agree button, they have probably already been defrauded by the creators. In the background, the fake downloader sends a premium rate SMS to the number based on the country of origin for the user. In order to distinguish people from all around the world, the malware contains premium rate numbers for 60 different countries in an XML file distributed with the application. Since the criminals probably wanted to make it harder for us to analyse, they used AES encryption to make the file “unreadable“. However when it is decoded, it reveals XML with a basic structure that for Czech Republic looks like this:

As you can see, the SMS is sent to the number 9030979 with this text „GET 9190002172+021=2plt3“ and is charged around 4$. Once this is done, user is redirected to the page „u*******i.org/content“ where the user is asked to give the content of the confirmation message.
This concept is actually nothing new in the Android malware world as the bad guys have been doing this in various ways for several months. However, AVAST makes it harder for them by detecting their work as an Android:FakeInst variation. So what is the lesson? Never trust weird looking alternative markets and always check the app permissions. If you’ve downloaded a game that asks for SMS and Phone calls permissions, it probably means that someone is about to “play you” instead.
Some samples and their SHAs:
4568c4f98fa376d2df382a42f2a6531d2f307572795bf30701a7b1e7a61fc4bb
99e93ad659447bbd279cc8a8db7d1a0ef435a7d92a89ba9fc040e0d0e3314a97
b7996591e0957d3ef36848f0c05fd4131138297606f39d609cb23b78a31d1c35