The “Unitrix” exploit takes several Unicode features designed for right-to-left languages and uses them to mask malicious executables as safe text or video files. Here is a short list of the main options.
 We described Unitrix in a recent release Hackers flip filenames to create "safe" file extensions. But, this was just the start of the detective work. Analysis of this exploit showed that the hackers do not directly takeover the infected computers. Instead, they have a “pay per installation” network that provides outsourced infection and malware distribution services for other cybergangs – apparently based in Russia and the Ukraine – after giving each infected computer its own identification number. And, this gang has the ability to change the final payload thanks to its downloader: rootkit today, tomorrow something else.
We described Unitrix in a recent release Hackers flip filenames to create "safe" file extensions. But, this was just the start of the detective work. Analysis of this exploit showed that the hackers do not directly takeover the infected computers. Instead, they have a “pay per installation” network that provides outsourced infection and malware distribution services for other cybergangs – apparently based in Russia and the Ukraine – after giving each infected computer its own identification number. And, this gang has the ability to change the final payload thanks to its downloader: rootkit today, tomorrow something else.
We’ve titled this malware W32:Fivfrom. It’s a malware downloader which, after activation, connects to several distribution centers to download and install malware to the infected computer. We analyzed over fifty separate files, all of which initially looked quite different. But when we looked inside, we found some similar patterns. All files were packed with UPX, and then there was a polymorphic loader which generated the final exe file. This means the malware contained two layers of protection - UPX as the first layer and a polymorphic loader for the second layer.
Here is the binary data at the entry point for two different samples. Although they look completely different, their output is always the same.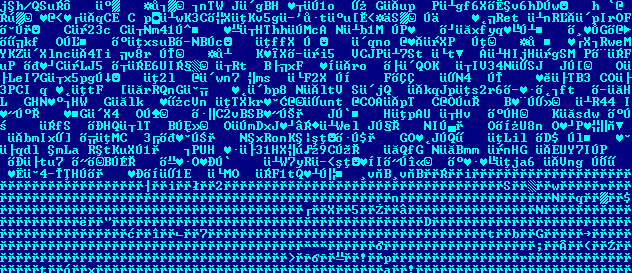
- Figure 2. Polymorphic loader 1
Although this may seem complicated, extracting the code of loader is very simple. In OllyDBG, put breakpoint on VirtualFree, and run the application. When the debugger stops, you will see this in your stack window:
0012F3BC 00921909 /CALL to VirtualFree from 00921907
0012F3C0 00970000 |Address = 00970000 <<<<
0012F3C4 00004400 |Size = 4400 (17408.)
0012F3C8 00004000 \FreeType = MEM_DECOMMIT
where memory block being currently unallocated contains the code of the downloader itself. Figure 4 shows the window of debugger at the moment when we can dump the original (unpacked and loaded) downloader.
As I mentioned, Malware Fivfrom is a downloader and individual variants may connect to a range of different URL addresses. It is assigned several URL addresses which serve as the source of commands for the downloader. The downloader specifies a request and obtains the reply stating which file to download and execute.
So far, we have identified three URL addresses:
- dns-grepfree.com
- armaturan.ru
- dateoncount.com
The request format is the same for all servers and looks like this:
<server>/<path>/ots.php?seller=<seller_id>&hash={<hash unique for each computer>}
From the URL format, we can deduce that this is pay-per-install network. Users who distribute malware (sellers) are assigned an ID. Every time a new computer is infected, this new unique hash and seller ID are reported to servers.
Examples:
- dns-grepfree.com/R3FG2mJsx0o4F/dl/ots.php?seller=3&hash={FEDBB4FD-AD01-4274-950A-674E7629C126}
- armaturan.ru/forum/dl/ots.php?seller=4&hash={1C9412AB-663E-4E68-928F-5F746C805150}
- dateoncount.com/pdloder/dl/getapp.php?seller=1&hash={40AA506C-76CF-4C01-A901-40A73168B17D}
After the URL request is sent, there is a server reply. Here is an example of successful reply to a request from dns-grepfree.com:
||485d4b022a359b9ebc841956bbdc0bc0||http://filmzone.org.ua/k.gif ||0||0||GBNTBBkA.exe||<br>
We can see that the reply contains link to the new URL and the name of new exe file. The downloader downloads this file (http://filmzone.org.ua/k.gif), renames it as GBNTBBkA.exe and executes. Although the newly downloaded file has a GIF extension, it is internally another MZ exe file.
Another step of our analysis was to look a little bit inside the file GBNTBBkA.exe. When we first executed this file, it quickly ended and nothing happened. After a deeper examination, we found out that GBNTBBkA.exe was a rootkit dropper. It dropped the file “yplv.sys” in c:\windows\system32\drivers\ and installed this newly dropped file as a new windows service.
After this service successfully started, the injected rootkit is able to hide. The yplv.sys file was no longer visible, although it was still present in the system. Figures 5 and 6 show the impact of the installed rootkit: Figure 5 shows the contents of system before rootkit is installed, the right figure shows after rootkit is installed and the presence of infection hidden.
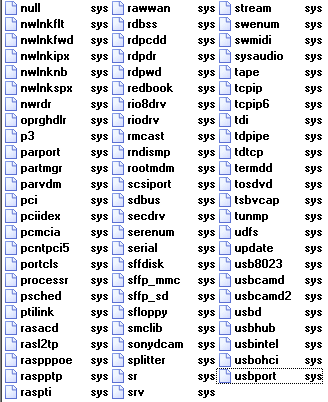
Another evidence of rootkit activity is output from the Rootkit Revealer program. We can see that (among others) yplv.sys is hidden from API.
So where does this take us? For the final user, the important issue is that they are infected with some malware that keeps its presence very, very quiet. On the way to this infection, the owners of this pay-per-installation network can change the payload of their downloader at any time.