File infectors are not on the top of their popularity nowadays (there's not a wide variety of them ITW, but the few active - such as Sality or Virut - are difficult to defeat). One reason is the frequency of their updates and the complexity of their polymorphism, another reason is the fact, that these viruses are not perfectly tuned. If the file infector should be successful (and transparent to the normal system behavior), it simply should not produce corrupted files (the process crashes will quickly point out what's going on). I will show you some examples of bugs in file infectors (below in this article). The problem is that these bugs often make the infected binaries uncurable.
Which file infector is the buggiest? It's hard to say, but my favourite one is Win32:BluWin with 4/10 corrupted files. Here are some screenshots to illustrate the way of making the victims unable to run properly:
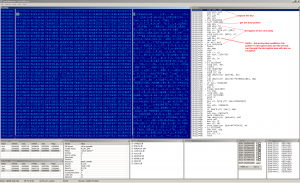
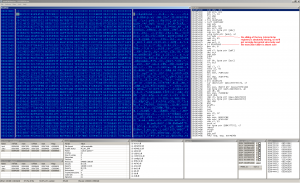
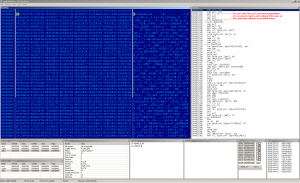
These bugs are randomly repeated in the infected samples. BluWin was never much widespread, but we can take a look at the big player - Virut. Virut infects 64bit binaries. First time I thought it is a feature, but - it's bug! Even this mighty creepy piece of malware has this weak point. The following picture can describe it:
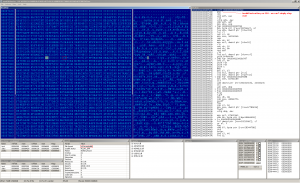
What can we see? We're in the 64bit binary, but Virut used its 32bit body. Since pusha instruction (60h) is not present on 64bit, there's always a problem when Virut tries to execute it. And what about inc/dec (their short forms are reserved for REX prefixes on 64bit). Is there at least one working 64bit Virut sample?