In our blog, we wrote several times about various types of Ransomware, most recently about CryptoLocker. In most cases, ransomware has pretended to be a program installed into a victim's computer by the police. Because of some alleged suspicious activities found on the user's computer, ransomware blocks the user from using the computer and demands a ransom to unlock the machine or files.
Different ransomware families have different graphics and skins, usually showing intimidating images of handcuffs, logos of various government and law enforcement organizations, policemen performing inspections, government officials, etc... You can read some of our previous analyses on our blog - Reveton, Lyposit, Urausy - are the most prolific examples of such ransomware.
In this blog post, we will look at the functionally of the same type of ransomware, but one which displays more annoying and disturbing photos. After showing the message saying, "Your computer has been suspended on the grounds of viewing illegal content," accompanied with the current IP address, name of internet service provider (ISP) and the geographical location, it displays several pictures of child pornography!
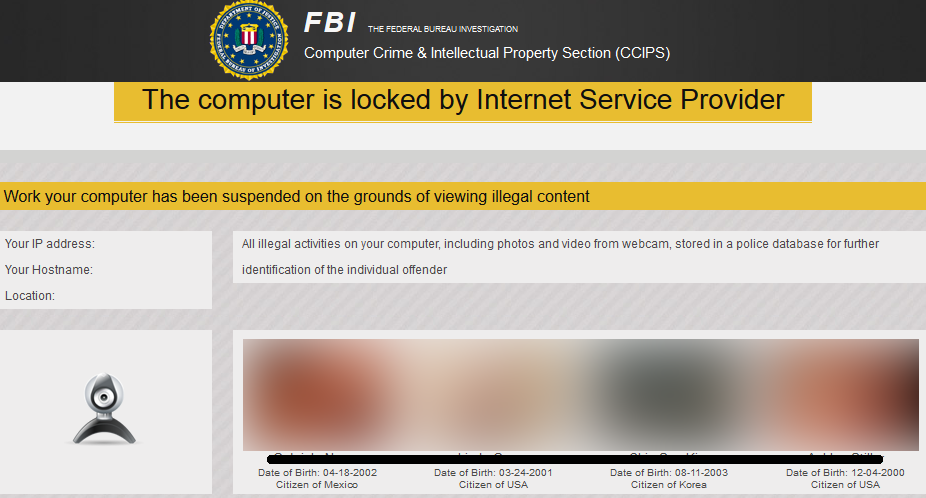
Printed below each image of an abused child is the child's name, birthday and nationality. Names, locations, and birthdays are probably made up, however from the pictures of the children, we can clearly see that they became part of activities which are illegal in almost all countries of the world.
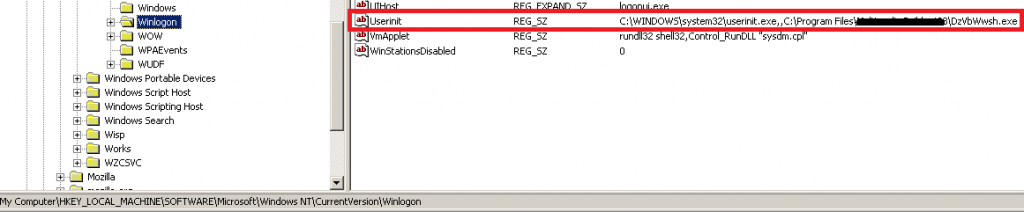
Now, let's look at the malware itself. After being executed, it modifies some well-known registry keys. In HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon, the data assigned to value "Userinit" contains the path to the copy of the malware itself. The malware is copied under a random name into a randomly chosen directory in "Program Files" folder.
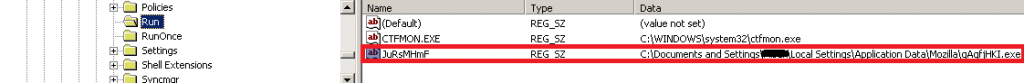
In HKCU\Software\Microsoft\Windows\CurrentVersion\Run a new randomly-generated value is added. This value points to a location in the "Application Data" directory where another copy of ransomware is deployed.
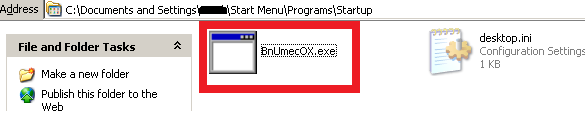
The third point of persistence is another copy of ransomware; this time ransomware is copied in the "Startup" folder.
Modification of multiple startup points ensures that even if the victim knows and removes it from one of the locations, other instances of ransomware will reinfect the location again and the system remains locked.
When examining resources of the executable file after removing the outer cryptor layer, we notice a resource item containing an IP address (red figure below), which is crucial in the following communication with the C&C server.
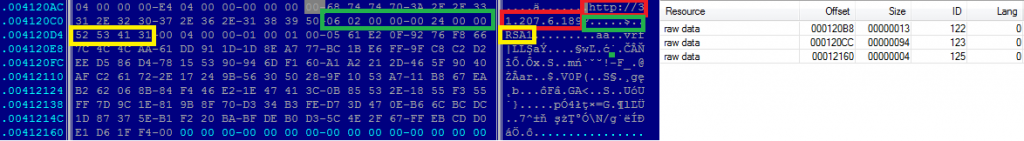
After the IP address, we notice a binary blob, which later contains the string "RSA1" (yellow figure above). The documentation gives us a hint that we are dealing with a public key (byte 0x06) and use RSA public key signature algorithm (bytes 0x00, 0x24, 0x00, 0x00, green figure above).
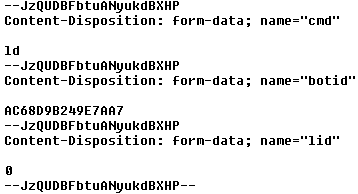
The C&C communication starts with sending a POST request with several randomly generated strings starting with "--", interleaved with strings like "cmd", "botid" and "lid". Botid is generated based on environment variables, lid is probably a request for "license id", and the ld command probably asks to download the custom payload, which is the website with disturbing pictures.
The downloaded payload is at first decrypted using RC4 cipher with the hardcoded password "impact."
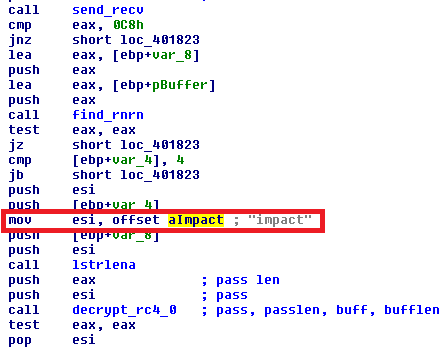
After the decryption, we can see the structure as displayed in the figure below. The first 4 bytes (in red) represent the license id (lid) variable, in our case it is 0x69306c1c, followed by three dwords which represent the lengths of the three consecutive payloads. The first payload is a zip archive (PK signature, in grey) containing the landing HTML page with pictures.

The second payload (red figure below) contains IP, ISP, and geographical information of the victim. The third payload (green figure below) is a blob containing the signature data to be verified with the public key mentioned above.

When installed on the system, ransomware creates a key in HKLM\SOFTWARE\{guid}, where it stores some of the obtained constants like ID, Landing (folder with the unpacked payload), LID and Personal (IP, ISP, Location).



While active, ransomware keeps the connection to the C&C server, which IP address was hardcoded in resources. Depending on the obtained reply, if the victim submits the correct code, the attacker can unlock the computer remotely. If this situation happens, the LockDisabled registry value in HKLM\SOFTWARE\{guid} is set to 1.
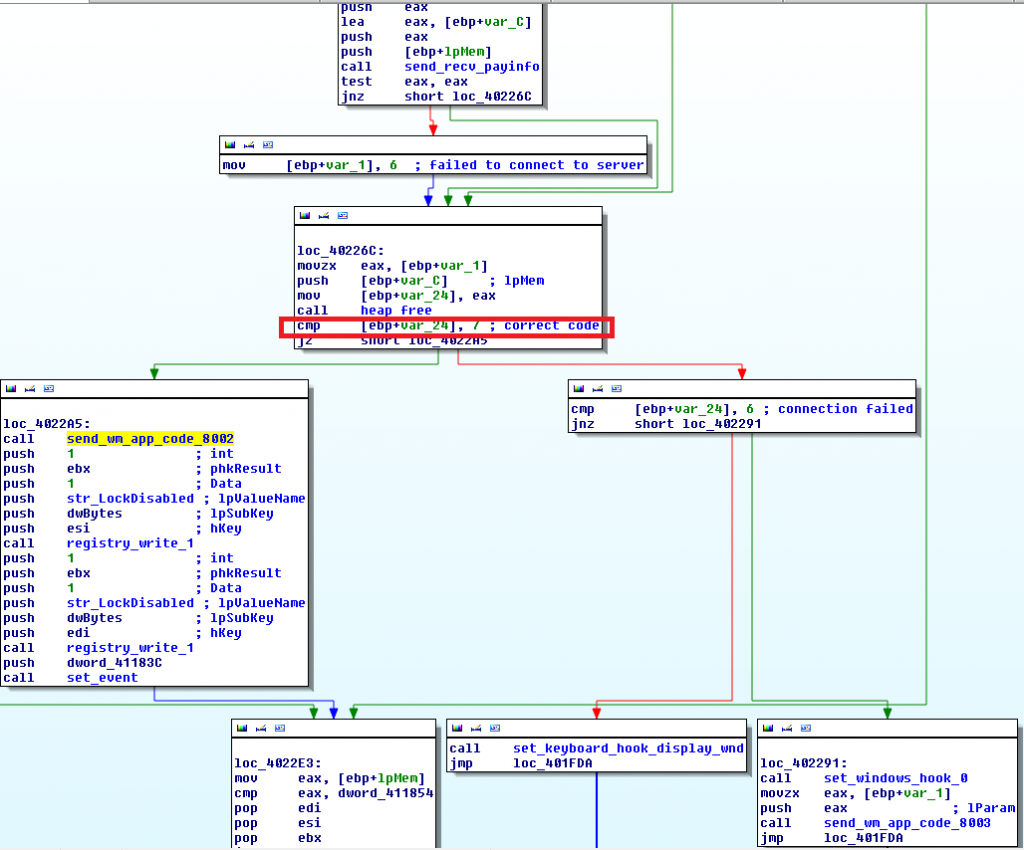
From the index.html belonging to the landing page, we can see that there are several defined status responses. Response number 7 (case 7), tells the user that, "The entered code is correct. Your system will be unlocked." You can see the comparison of the received code "7" in the red figure above.

Except for the disturbing pictures displayed on the top of the screen, the victim can scroll down and read some interesting information about their computer. One box shows a fake log from their IP address visiting a site with inappropriate contents. You can see GET request followed by the name of the picture (explicit names were masked) to a non-existent domain childvideo.com. This log should be proof that something illegal really happened on the victim's computer.

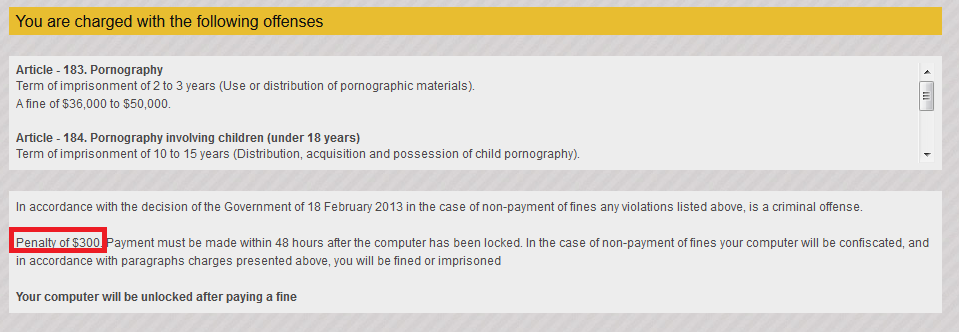
Later on, the ransomware tells the victim what criminal offense they committed and asks to pay a "penalty" of $300.
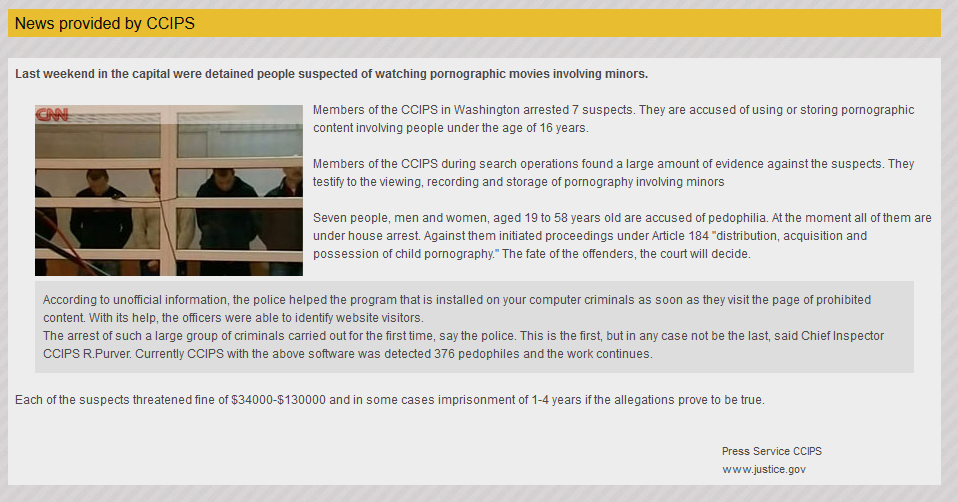
It also shows some "News from CCISP" (CCISP stands for Computer Crime and Intellectual Property Section.) In this given example, it tells a story of several people who have been detained and arrested thanks to the "program that is installed on your computer." We learn, from the poorly written text, that all the detainees face heavy punishments. Website justice(.)gov is mentioned as a source of this news. When you try to find this news, unsurprisingly, you won't find any relevant reference.
The last part is the box with a form for payment of the fine. Either MoneyPak or paysafecard are accepted. Below each logo of the accepted payment system, the ransomware helpfully tells you where you can buy these cards, if you do not know where to get them.

Conclusion:
Ransomware is right with the initial message that "something illegal was found on your computer." Images of child pornography can be really found on the victim's computer, because the ransomware downloaded and displayed them. It would be an interesting question to ask lawyers - to what extent is a victim of ransomware responsible for the contents being displayed on her screen?
What to do if you have ransomware
An infected machine can be manually disinfected by booting the system from external media. With this in mind, you can use avast! Rescue Disk, included in all avast! 2014 products, to create an image of your avast! installation. Delete all the copies and their references in the registry keys as mentioned in the persistence section. Read more about avast! Rescue Disk here.
SHAs:
A6CDBEC2B3152CE9242500E39EDAD7273B107080FF925F814AB449904373B4BB
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.