Win32:Reveton-XY [Trj] saves hundreds of computers worldwide and cybercriminals know it!!!
It has been more than a year, since we last time reported about Reveton lock screen family. The group behind this ransomware is still very active and supplies new versions of their ransomware regularly.
Recently we obtained a heavily obfuscated sample. As in most other cases we started with the examination of the sample. Except for the regions with a high entropy interleaved with regions with constant (usually zero) bytes, we noticed an interesting string, Win32:Reveton-XY [Trj], within the body of the obfuscated executable file. It is not possible to tell what sort of malware is inside without unpacking or executing the obfuscated file, however in this situation the authors are indicating that Reveton might be inside.
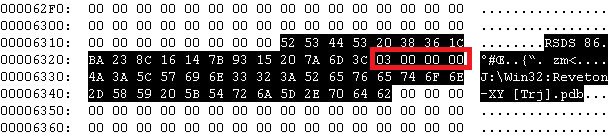
When we look at the selected region in the figure above, you can notice a marker RSDS, followed by some binary data, after which .pdb file name is appended. According to the documentation, this block of data is referenced in IMAGE_DEBUG_DIRECTORY structure, which is a part of the executable file header .
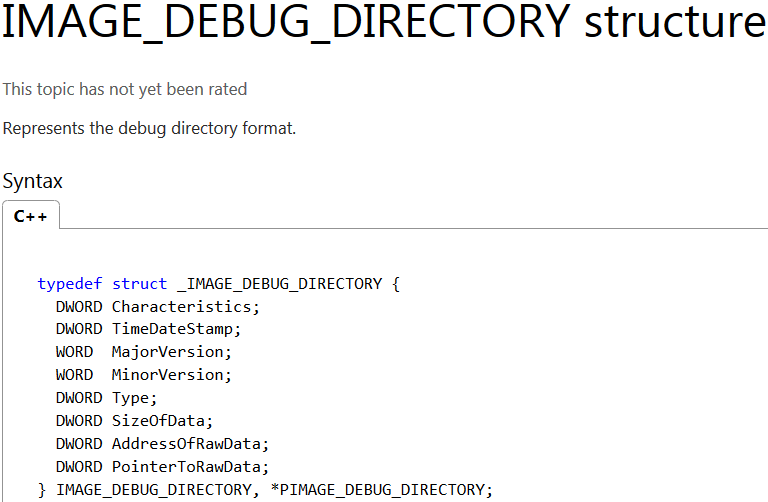
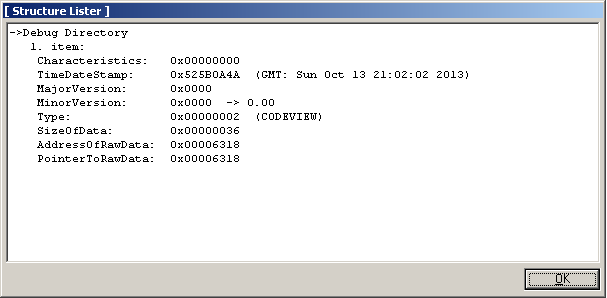
RSDS format has a simple structure, as you can see in this article. The RSDS signature is followed by a 16-byte globally unique identifier, 4-byte age, and a zero-terminated pdb file name. Age is incremented each time the project is remade by linker. From the figure above we can see that the Reveton packer was recompiled three times before being released to the public.
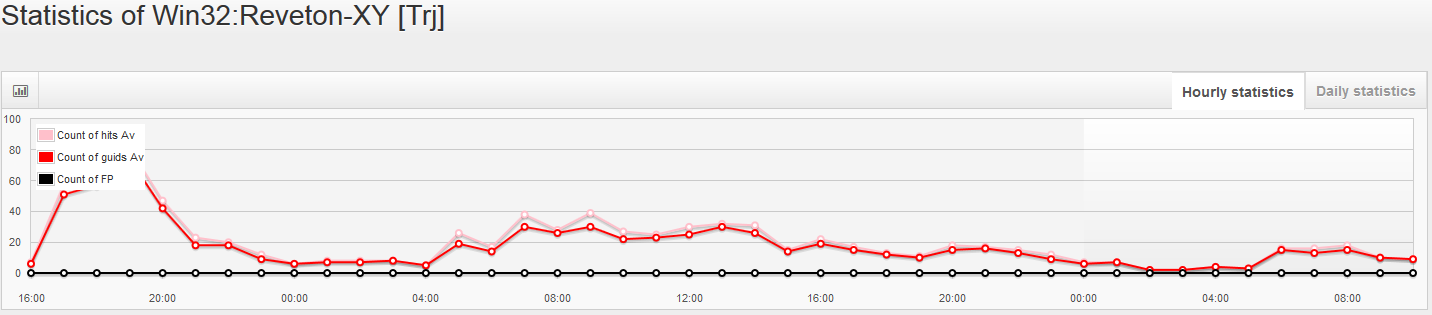
Different antivirus companies use different detection names for the same or similar malware families. It is probably not a coincidence that detection of Win32:Reveton-XY [Trj] is mentioned in RSDS section. This detection name belongs to AVAST, and as we can see from the hourly and daily statistics, it is a quite successful detection, which saved hundreds of computers from being locked.
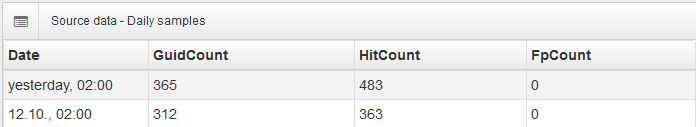
Geographical distribution of IPs saved by Reveton-XY shows us that the most affected countries are the western European ones, particularly Germany, UK, France and Italy, followed by the US and Australia as major non-European English speaking countries. We detected no hits in Russian speaking countries, which are probably the countries where the attackers came from. Western European countries and other English speaking countries are generally preferred by cybercriminals, because they are more likely to generate higher revenues.
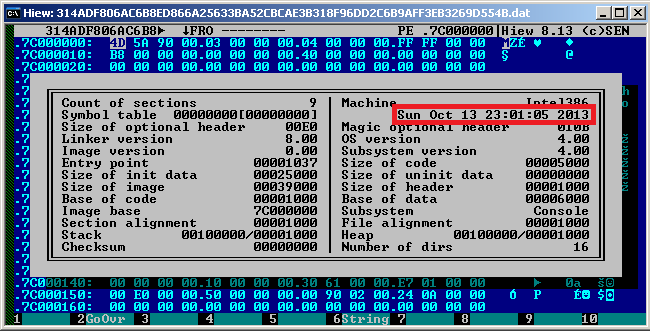
Let's look at Reveton ransomware itself. A quick static analysis shows that the cryptor was compiled in the middle of October 2013.
After performing the deobfuscation and getting the clean version of malware, we can see that it is a dynamic linked library (.dll) with a few exported functions, named GL30X.
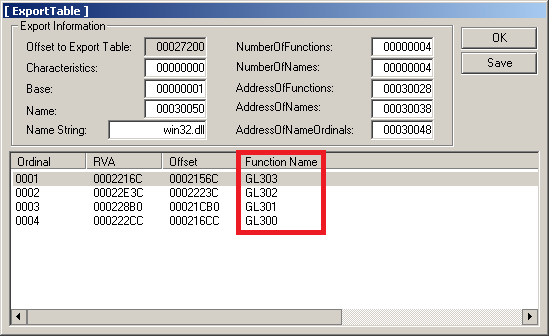
First of all, DllMain is called. It performs a check whether the file runs in a virtual environment or not. This check is done by searching for suspicious strings in the output of EnumDisplayDevicesA.
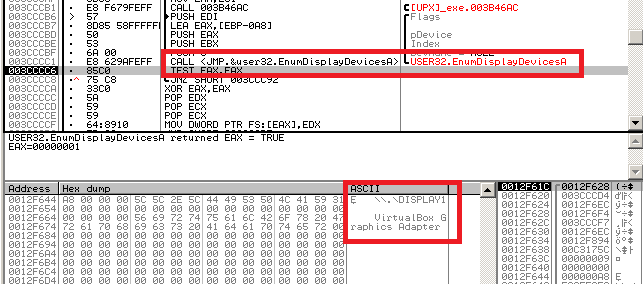

When any of the mentioned strings are found (VIRTUAL, VMWARE, VMBOX), the malware terminates itself. Malware then copies itself into All Users\%APPDATA% directory and executes itself again via rundll32.exe. It copies itself under a random name (with extension .plz). There will be more than one instance of running malware, so Reveton creates a file with extension .pff, size 12600 bytes, in which it stores the data which will be shared among several running instances of Reveton (PID of the initial process, IP addresses to which it connected to...).
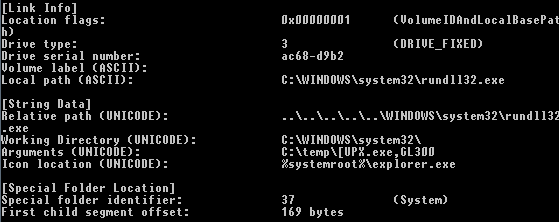
GL300 exported function spawns several threads. There is one thread for managing persistence via dropping a LNK file to the startup folder (%USER%\Start Menu\Programs\Startup\). The figure below shows a parsed LNK file. After reboot, rundll32.exe starts malware by calling its exported function GL300.
The second point of persistence is achieved via modifying "HKLM\SYSTEM\ControlSet001\Services\winmgmt\Parameters" registry key. Old value "ServiceDll"="%SystemRoot%\system32\wbem\WMIsvc.dll" is replaced by the path to malware dll.
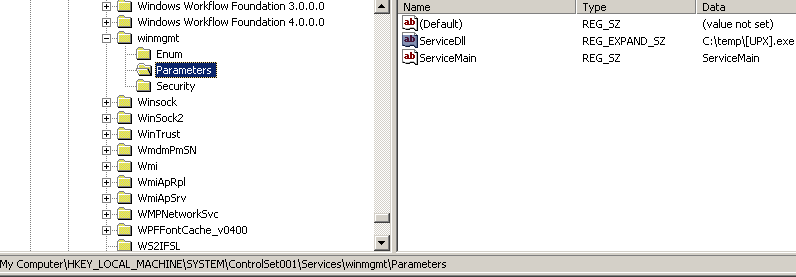
According to the documentation, winmgmt is a service which automatically starts when the first management application requests connection to a WMI namespace. By modifying these registry settings, Reveton ensures that its persistence via registry stays unnoticed longer. Most malware modifies the Run registry key (Software\Microsoft\Windows\CurrentVersion\Run in HKLM or HKCU), which is a widely known location a user looks when examining which programs get executed at startup.
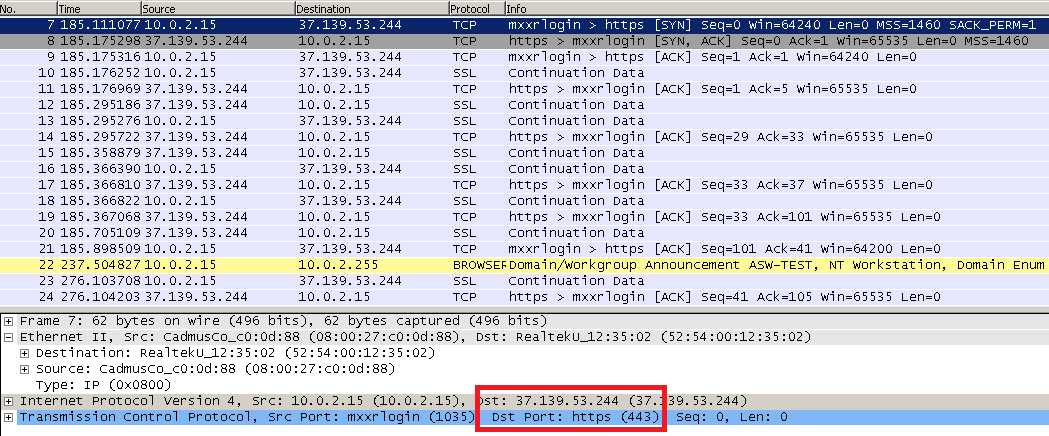
The most important thread is the thread which downloads the payload, which then locks the computer and displays a ransom message. From the network analyzer screenshot, we can see the communication between the victim's computer and the attacker's server. The communication initiates from the victim's port 1035 and goes to the destination port 443, which network analyzer marks as http (http secure).
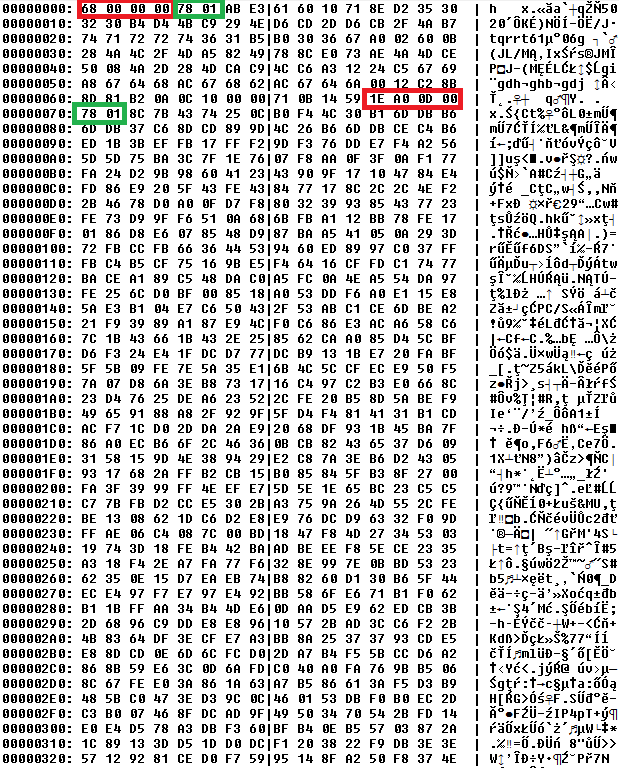
The question which came to our mind was, "Does Reveton really communicate via SSL?" A quick look at the downloaded payload gave us the following answers. The first double word has value 0x00000068 (68 00 00 00), which contains three zeroes and it is very unlikely that an encrypted data stream would have three equal consecutive bytes. The following two bytes are 0x0178 (78 01), which might look like zlib compression header. Suppose that the first number 0x00000068 (68 00 00 00) is the length of the following zlib-packed data block, we get to offset 0x68 + 4 (size of the length field) = 0x6c, which contains a double word number 0x000da01e (1e a0 0d 00), followed again with signature 0x0178 (78 01). In the figure below, see the block lengths in red oblongs and zlib headers in green oblongs.
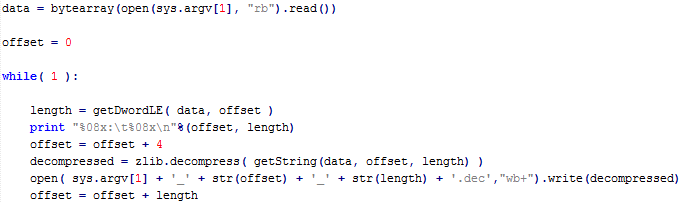
The following simple python script will do the job of extracting and decompressing all data from the received payload.
Two files get extracted. The first one contains basic geolocation information like the city, country and IP address, the second file contains a block starting again with the double word value 0x0178 (78 01). Could it be zlib compression again?

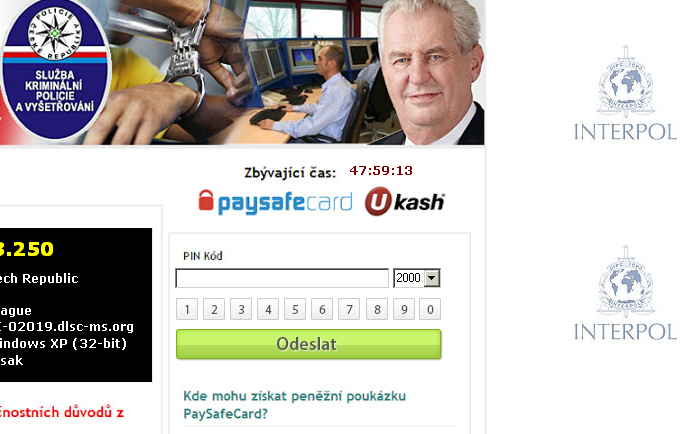
Yes. After applying zlib decompression one more time, we got the executable file, compiled in Delphi, containing the following interesting forms. It clearly displays a warning message, supposedly from the police, and a form for entering paysafecard or ukash credentials. The profile photo in the right upper corner belongs to the president of the country in which victim gets infected. The screenshot below shows a photo of the president of Czech Republic. "Malware don't need Coffee" blog published even more screenshots from more countries, including even the US president.

Notice the default IP address in the form above. 109.105.134.11 points to aion-frost-01.ti.msk.inn.ru, which is an IP belonging to the Russian range.
Unlike other ransomware such as Urausy or Lyposit, which download HTML pages with images and display them in maximized Internet Explorer window with hidden controls, Reveton downloads a binary file, which imitates the browser window.
SHA256:
314ADF806AC6B8ED866A25633BA52CBCAE3B318F96DD2C6B9AFF3EB3269D554B
71DA770631E8F778F6CB6EBB9BB23D8B1F518911B0EEA4F9AB5A4E04489EB3A0