Grum, one of the largest spamming botnets, suspected to be responsible for over 17% of worldwide spam (as described here), which was "killed" in July 2012, still lives. We have been tracking its activity since January 2013. We can confirm spiderlab's doubts about the grum killing published in March 2013. The following article provides some details about registered grum activity.
We have seen grum activity on following sites:
- servercafe.ru
- hub.werbeayre.com
- sec.newcontrrnd.com
- sec.convertgame.com
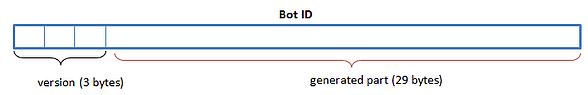
Every bot client generates its own identification number (ID) on its first run. The length of the ID is 32 characters. The first three correspond with a bot version and the other 29 characters are randomly generated. It is also set to the HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\BITS\ID registry key, which is queried on every run.
After the bot sets its ID, it tries to connect to a C&C server.
1) The bot contacts C&C server with a HTTP GET request to get the FQDN of the client's computer
http://%server/spm/s_get_host.php?ver=%botVer
2) The information is used to contact one of the SMTP servers obtained from DNS MX records from following domains which are used for sending spam:
- hotmail.com
- yahoo.com
- aol.com
- google.com
- mail.com
- mail.ru
- yandex.ru
- …
3) Then the C&C server is contacted by the following request
http://%s/spm/s_alive.php?id=%botID&ticks=%u&ver=%botVersion&smtp=%s&sl=%d&fw=%d&pn=%d&psr=
The smtp variable is set to ‘ok’ when the bot successfully contacts one of the SMTP servers and set to ‘bad’ if it does not.
4) The C&C server answers with a message which looks like a typical BASE64 encoding
For example:
Xu6hQoZL5+9/Hva9N3F3A2+gwPdLuk28BPA5Alm1IOS9MWvCLGp9r/UEqHksCNo4djEmA8SBk/tPRNvg1wc1rjZnwToThUorVw7kdU/h53sgoszvg0OX06MFQvEOxLqF7P4PQ+s=
Actually the message is encrypted by RC4 algorithm with key equals to the bot’s ID and then it is encoded by BASE64.
parts of low level BASE-64 decoding
low level decryption part of RC4
The whole decryption algorithm written in C# could look like this:
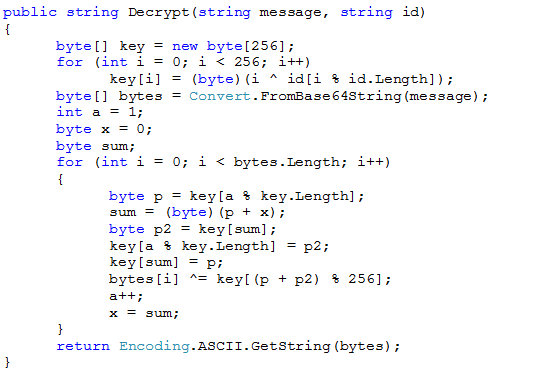
The bot id is 72176717204370682282907051332175 for the mentioned message.
After decryption process we can see the message:
http://84.200.70.131:9091/spm/s_task.php?id=72176717204370682282907051332175&tid=61853
5) The bot remembers the ot variable and sends the HTTP task request without the ot variable.
http://84.200.70.131:9091/spm/s_task.php?id=72176717204370682282907051332175&tid=61853
6) The C&C answers with spamming instructions including spam mail template which is also encrypted by the schema mentioned above.
The interesting thing is that sent spam is similiar to scam described on our blog in the past.
Finally, we provide a screenshot of encrypted instructions, a spam email and an example of decrypted instructions .
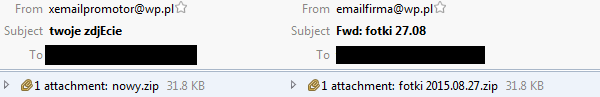
example of sended spam
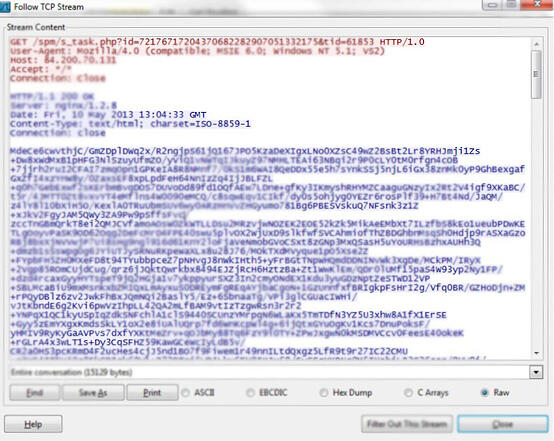
encrypted spam instructions
<info>
taskid=61853
realip=x.x.x.x
dns=8.8.8.8
hostname=y
heloname=y
maxthread=25
from=usypc@ozucfx.net
type=0
try_tls=0
use_psr=0
use_dnsapi=1
try_mx_num=1
use_ehlo=1
</info>
<emails>
nadialee@hanmail.net
nadialee@hellokitty.com
...
nadialeitao@zipmail.com.br
nadia_leonita@yahoo.co.id
</emails>
<ac_list>
</ac_list>
<text>
Received: by work.ozucfx.net (Postfix, from userid %W_RND_INT[3])
id E%W_RND_INT[2]CE%W_RND_INT[5]E; %DATE
From: Work at Home <%FROM_EMAIL>
To: <%TO_EMAIL>
Subject: Your second chance in life just arrived
Mime-Version: 1.0
Content-Type: text/html; charset=us-ascii
Content-Transfer-Encoding: 8bi
Precedence: bulk
Message-Id: <%GMTDATA[yyyyMMddHHmm].E%W_RND_INT[2]C%W_RND_INT[5]F@web.ozucfx.net>
<html>
<body>
...
</body>
</html>
</text>