Not everyone appreciates an avast! warning. Some IT professionals find it hard to believe that an infection has taken place on the computers and the networks under their supervision.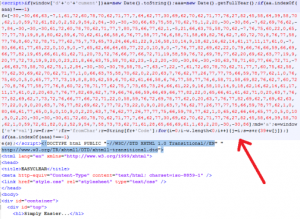
“In today’s update you have included their website as being infected and harmful,” complained one web developer in an email to AVAST Software. “For the last month, it has been a brand new site. I have scanned the site with several online website scanners and they all come up clean.”
AVAST Software sends out a lot of warnings to users. During January of 2012, we recorded 1.87 billion incidents of our users encountering malware.
In this specific case, the company owners had avast! on their own computers and they were getting warnings that their site was infected. Even worse, because their avast! was blocking them from accessing their own site, they realized potential customers were also getting shut out – costing them money.
While online scans from two other security suppliers did not detect anything, Jiri Sejtko at the AVAST Virus Lab did. He found evidence of a BlackHole Exploit Kit attack that had taken place three days previously. The script shown in the image redirects visitors to web-media-stats-analyse.[REMOVED].php?id=07a1509e7e5d828d, a well-known malware distribution domain.
Sorting out this particular infection has required some cooperation between the site developer, the hosting company, and the owners. While the specifics vary for each website, Jiri pointed out four most common sources of malware infections:
- 1. Old and vulnerable software (e.g. old versions of WordPress, Joomla,...) and plugins for this software.
- 2. Plugins and themes downloaded from untrustworthy sources (already contains infections or backdoors)
- 3. Weak passwords.
- 4. Stolen passwords.
To reduce these vulnerabilities – and uncover existing infections, using the “AVAST 5+3 Steps” can help site owners both to increase network security and to uncover any existing issues:
- Software - Keep your WordPress, Joomla or whatever you use up to date.
- Plugins - Check versions of the software/plugins used on the website. Download only from trusted sources – don’t use greyware (warez).
- Passwords - Change and make all passwords stronger (at least 10 characters long including symbol keys (@#$%%^).
- Secure - Do not access the website through unsecured ftp connections.
- Save - Do not save passwords in ftp clients.
Once you got infected or you suspect something bad is going around, you should also:
- Inspect – Check out your connection logs...
- Log - Set logging (if not already set) to enable you to find who attacked and from where
- Look - Check carefully at your website for strange php files - backdoors - usually short and simple php scripts allowing easy access to anyone without a password. They are primarily located inside the img/image/images directory, but not limited to that directory. Check your scripts for encrypted pieces of code. Everything such as 'eval(base64_decode("...."));' or 'eval(gzinflate(base64_decode("....")));' needs to be inspected.