Win32:Abigor is a complex file infector consisting of the replicating part, a backdoor and a keylogger. Its source is known, but it is interesting to look at the file also from the other side.
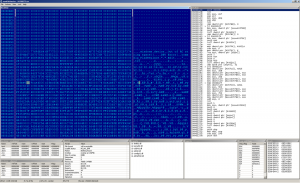
The redirection to the virus body is done by hooking the reference to ExitProcess or CRT _exit function. We can see the push + ret redirection in this case. The rest of the code remains untouched, the virus itself is injected to the last section. Here we go:
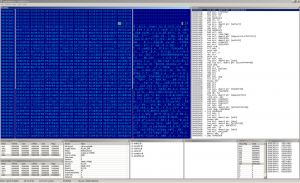
The virus body is highly obfuscated, it contanins only few instructions needed to decrypt the payload and many garbage instructions. This technique makes the emulation of decryptor quite slow. Anyway, after a bit of time we can get the decrypted code and data.
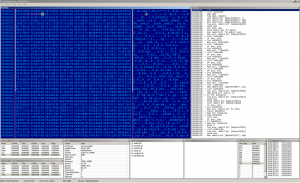
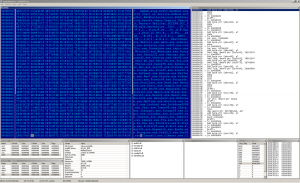
The first picture shows the decrypted code, which performs the loading of kernel32 and checks a breakpoint on GetProcAddress. The second screenshot contains the list of AV services, which are suspended by the virus and the list of files, which are patched to do nothing. As mentioned above, the file infector comes along with a backdoor engine, which begins on the next picture.
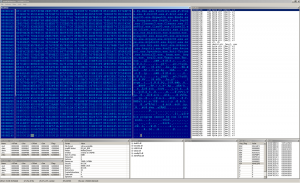
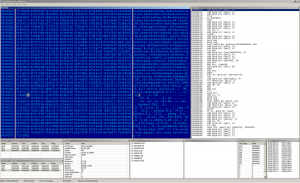
There's the rest of the killed AV executables and the embedded PE binary on the picture above. The other picture contains the signature of the virus creator. Now it's time to dump the binary and take a separate look on it.
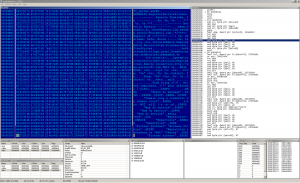
The binary was compressed with UPX. After unpacking it we can see some interesting strings from the backdoor engine. There's also a reference to the keylogger (a hooking function from embedded library). Another interesting strings are shown on the next screenshot.
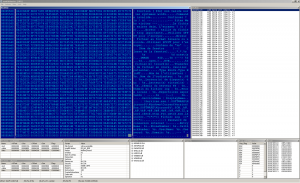
Last part which can be a bit interesting is the embedded keylogger. Let's look at the last screen.
The very last thing is the detection coverage of the binaries. Here are the results from virustotal: http://www.virustotal.com/en/analisis/eba51e28a8b24940f01a9aff3efa6e44 http://www.virustotal.com/en/analisis/89492671981914813c171e28553aea37 http://www.virustotal.com/en/analisis/c4b265d21eedd7b708f4eed699c5026f http://www.virustotal.com/en/analisis/fd10ac0af93949b5b7b44420aafaca53