Several days ago we received a complaint about javascrpt.ru. After a bit of research, we found that it tries to mimic ajax.google.com and jquery, but the code is an obfuscated/packed redirector.
After removing two layers of obfuscation, we found a list of conditions checking visitors' user Agent. From these conditions. we got a clue and focused on mobile devices.

It all starts when a user start browsing internet from their mobile devices. They visit a legitimate site that's been hacked. This site contains a link to the site javascrpt.ru, where visitors' browser data is sent. If script hosted at javascrpt.ru recognizes the visitor's user Agent string as one of the list of conditions, the visitor is redirected to the malicious site, usually hosted at legitimate hosting, distributing malicious files for mobile devices. When users reach this site, the drive-by download starts. We found different behaviors for different devices.
For non Android mobiles, a file called load.php ( 2DECBD7C9D058A0BFC27AD446F8B474D99977A857B1403294C0D10078C2DB51D ) is downloaded, though in a fact it is a regular Java file. But as you can see our users are well protected:
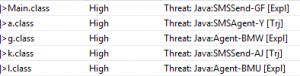
But the question is what is really happening with an unprotected user?
After running this file, the user expects a running application that they started, but in this case a list of agreements appears. And the first line is 'To gain access to content, you must agree to the terms presented below'. And what are those terms?
1. To gain access to the Service wa**y.ru/ content to make payment by sending up to 3 SMS messages
2. For complete information on pricing, it can be found at the web site: www.mo****1.ru/ (This site doesn't work right now )
Both Android and other devices are sending SMS to the Russian premium numbers
NUMBER = "7255";
NUMBER = "7151";
NUMBER = "9151";
NUMBER = "2855";
After sending SMS, just a simple ICQ application is downloaded from same site: *REMOVED*/land_paysites/files/icq.jar
To show better what happens when this site is reached from an Android device, you can check the next screenshots.
At first, a file called, e.g., browser.apk (94FDC9CFD801E79A45209BFDC30711CB393E39E6BF2DD43CE805318E80123C14) is downloaded to the device -- without the person's knowledge.
You can see in the install window that this application wants access to suspicious services that cost you money. Even in application permissions you can find suspicious permissions for your messages and directly call phone numbers that can cost you money, too. But fortunately avast! stops this application before it can cost you a huge amount of money.
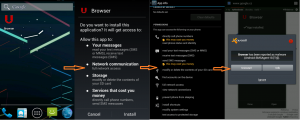
If a user install this application, its behavior is very similar to non-Android devices. Device sends pay text messages to those numbers and then downloads and installs a basic Dolphin browser from h***t.ru/land_browsers/files/dolphin.apk
Users should be really careful if they found in theirs mobile device some unknown application. Fortunately everybody can read where application will get access to but unfortunately a lot of users don't really pay attention to required permissions and it can cost them a lot of money but using good antivirus can help them to be protected.